Turning URL Investigation into Instant Understanding
In modern security operations, speed and clarity matter more than ever. Analysts are inundated with URLs in alerts from anything that touches the internet, and each one represents a potential risk that must be assessed immediately. The challenge is not access to telemetry, but access to the right context at the right moment.
That is where ThreatConnect and its Polarity product change the equation.
With the alphaMountain integration in Polarity, analysts gain real-time URL threat intelligence without ever leaving their workflow. The result is faster decisions, higher confidence, and dramatically reduced investigation friction.
Polarity as the Intelligence Delivery Layer
Polarity is designed to surface intelligence in context. Instead of forcing analysts to copy and paste indicators into external portals, Polarity overlays relevant threat data directly onto what the analyst is already viewing—whether that’s a browser, email, ticket, or investigation note.
By integrating alphaMountain, Polarity becomes a direct conduit to real-time URL risk assessment. When a URL is highlighted or searched, Polarity automatically queries alphaMountain’s ThreatYeti API and returns a concise but information-rich view of the threat landscape surrounding that URL.
This approach aligns with how analysts actually work: quickly, iteratively, and under pressure.
Immediate Signal, Not Analytical Noise
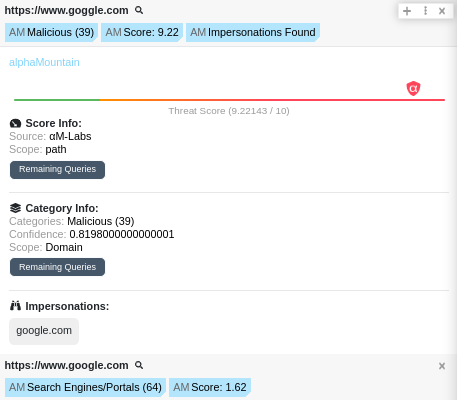
One of the most valuable aspects of the alphaMountain integration inside Polarity is the way it communicates risk. Instead of presenting dozens of conflicting verdicts, alphaMountain provides a single, high-fidelity threat score that reflects the overall risk of the URL.
At a glance, analysts can see whether a URL is associated with malicious infrastructure, how severe that risk is, and whether impersonation activity has been detected. This summary context allows an analyst to immediately determine whether a link warrants escalation, blocking, or deeper investigation.
The experience is intentionally designed to answer the analyst’s first question instantly: “Do I need to worry about this?”
From Overview to Explanation in One Motion
When more detail is needed, Polarity allows analysts to drill into alphaMountain’s enrichment without breaking focus. The expanded view surfaces additional intelligence that supports confident decision-making.
This includes category assignments drawn from alphaMountain’s 89-category domain classification taxonomy, giving analysts insight into the nature and intent of the URL beyond a simple malicious or benign label. Understanding whether a domain is linked to phishing, malware delivery, impersonation, or another risk class is critical for both response and reporting.
By presenting this information as a narrative context rather than raw telemetry, the integration reduces cognitive load while increasing analytical confidence.
Impersonation Context That Stops Phishing Faster
Brand impersonation remains one of the most effective techniques used in phishing and social engineering campaigns. The alphaMountain Polarity integration makes impersonation findings immediately visible alongside the URL itself.
When a URL is attempting to mimic a known brand or trusted domain, that signal is surfaced directly in Polarity. Analysts no longer need to infer intent from domain structure alone or pivot to separate brand-protection tools. The impersonation context is simply there, exactly when it matters.
This capability is particularly impactful for SOC teams handling phishing response, executive protection, and customer-facing brand abuse incidents.
Built for Real Security Operations
What makes this integration powerful is not just the data, but the delivery. alphaMountain provides real-time, high-fidelity threat intelligence. Polarity ensures that intelligence appears precisely where analysts need it.
Together, we eliminate unnecessary pivots, reduce investigation time, and enable faster, more defensible security decisions. This is especially important as teams move away from delayed or crowdsourced intelligence sources and toward signals that can be trusted for automation and enforcement .
A Clear Advantage for ThreatConnect Customers
For ThreatConnect customers, the Polarity integration with alphaMountain represents a natural extension of the platform’s mission: operationalizing threat intelligence. It transforms URL analysis from a manual, multi-step process into an immediate understanding of risk, intent, and context.
In an environment where seconds matter and analyst attention is scarce, that difference is not incremental—it is decisive.
Try alphaMountain in Polarity for Free
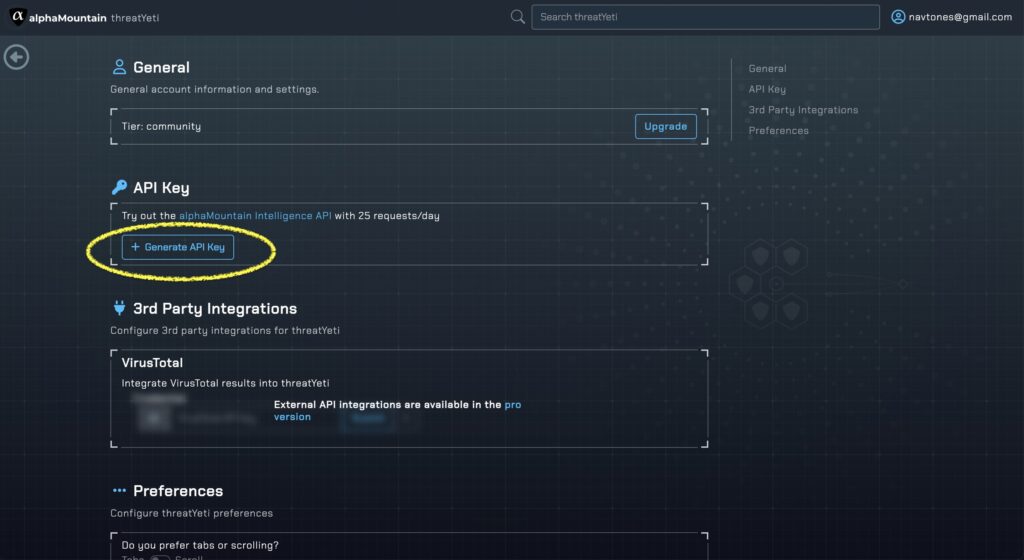
You can get a free alphaMountain API key by visiting threatyeti.com and creating a Community account.
From there, just click Username > Settings > Generate API Key and you’ll be all set.
ThreatConnect Polarity also has a Community edition which you can sign up for here.