
by Will Andre | Feb 2, 2026 | Blog
Turning URL Investigation into Instant Understanding In modern security operations, speed and clarity matter more than ever. Analysts are inundated with URLs in alerts from anything that touches the internet, and each one represents a potential risk that must be...

by Will Andre | Jan 25, 2026 | Blog
Since we launched threatYeti in 2023, we’ve seen the security community embrace our real-time search engine for risky domains and IP addresses. With our comprehensive intelligence, threatYeti has become a go-to replacement for the web-based versions of tools like...

by Will Andre | Jan 16, 2026 | Blog
We’ve spent years working with security teams that rely on VirusTotal every day. We understand why it became foundational: it made URL, domain, IP, and file analysis accessible in a single workflow, and it gave analysts a fast way to sanity-check suspicious...
by Will Andre | Jan 3, 2026 | Blog
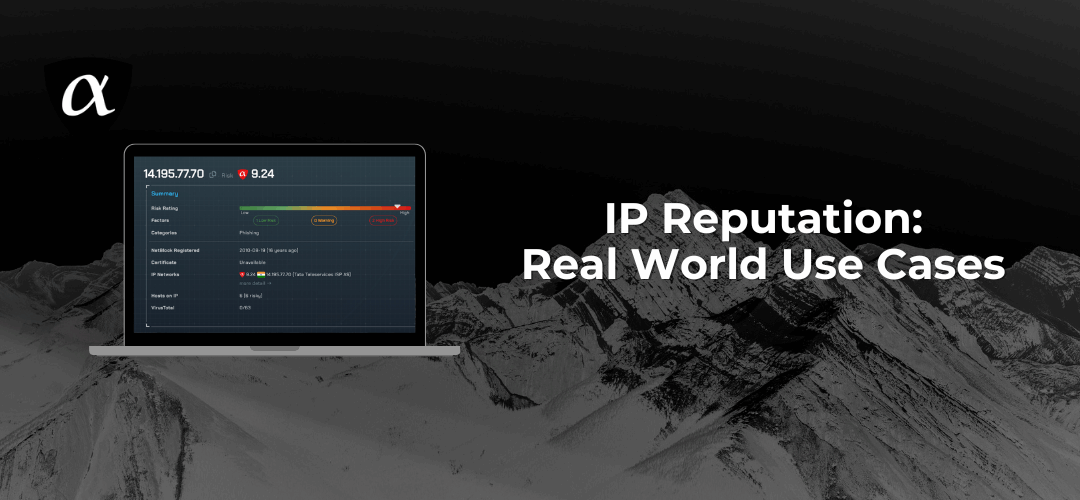
IP reputation used to be something analysts checked manually when an alert looked suspicious. Today, it’s a decision engine, quietly influencing what gets blocked, escalated, or ignored across the security stack. At its core, IP reputation answers a simple question:...
by Will Andre | Nov 9, 2025 | Blog
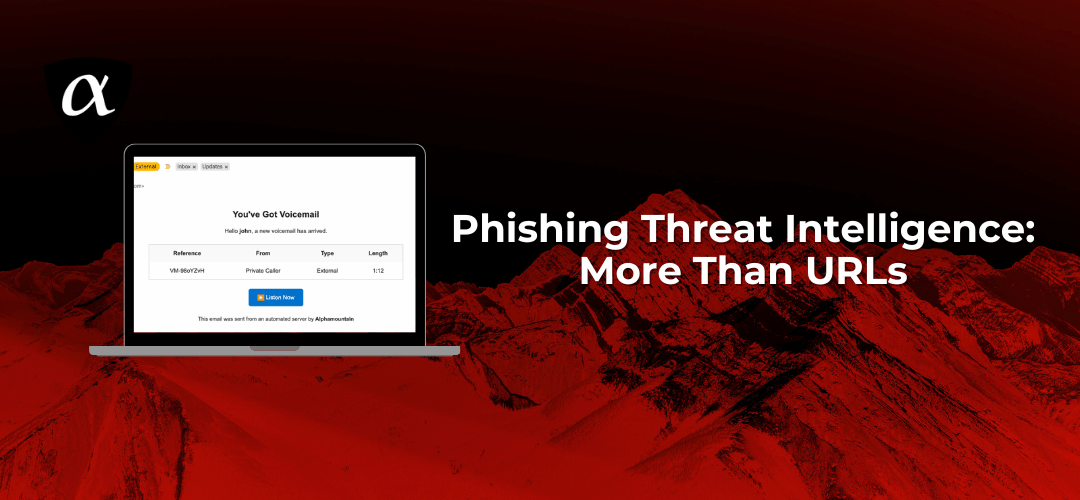
Phishing has always been about deception, but today, it’s not just about a fake email. It’s about obfuscation and infrastructure. Attackers now build entire ecosystems of redirectors, cloud storage, and short-lived domains to host credential-stealing pages. The result...
by Will Andre | Oct 31, 2025 | Blog
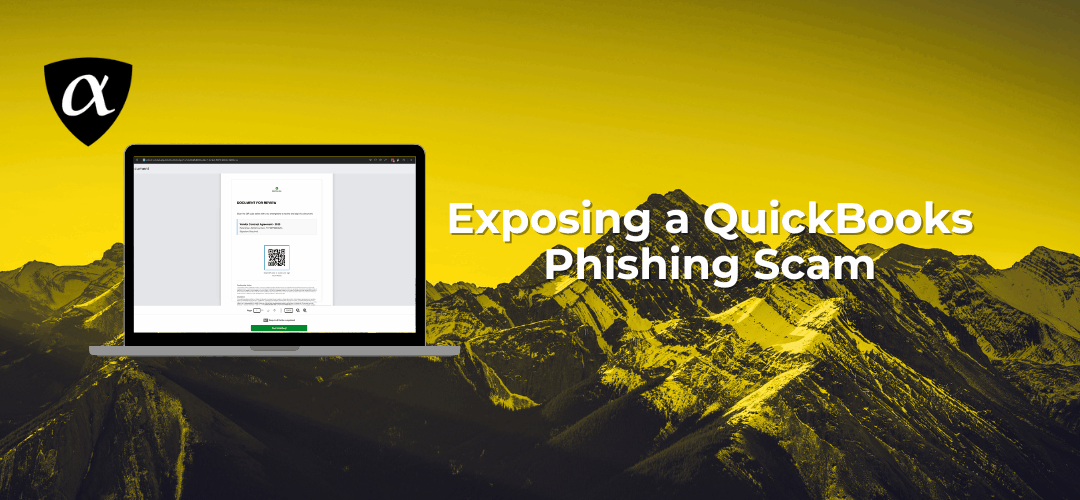
Phishing detection is a fast-moving game of cat and mouse. We recently received a message from the popular QuickBooks accounting software which turned out it was a phishing scam. Let’s take a deep technical dive into how threat actors are leveraging legitimate...







