Cybersecurity opinion is unanimous, for once
It’s rare, but every so often, the cybersecurity community locks arms and stands in solidarity against a common threat. This is usually in response to some large-scale compromise such as the recent events involving Solarwinds, Kaseya, or if you go a little further back, Wannacry. These were watershed events in the security industry because they leveraged novel attack vectors to maximum impact, the act of which always causes the industry to sit up straight in near-perfect unison.
The superhero moments that many cybersecurity dreams are made of are actually few and far between, but when there’s a good fight to fight, we turn up in numbers.
NOTE: If you came into this article for the tutorial on how to check if a .zip or .mov domain is malicious, go ahead and skip to the ‘How to’ section. If you’re up for a little background on how we got here, keep reading.
Google raises eyebrows
It’s odd, then, that the latest call to arms is in response to actions taken by none other than the almighty Google. On May 3, 2023, Google announced in a blog post that they were launching eight new top-level domains (TLDs) that would ostensibly increase the domain namespace available to certain online niches. The new TLDs are .dad, .phd, .prof, .esq, .foo, .zip, .mov and .nexus Almost immediately, the cybersecurity vox populi locked arms against two of these TLDs, .zip and .mov.
If you’ve been anywhere near a computer in the last five years, you know that the number of phishing and malware campaigns being launched are at all time highs, with no signs of slowing down. Phishing happens when illegitimate sites pose as legitimate sites for the purposes of stealing credentials to compromise accounts or entities. Malware is malicious software that can be delivered as a file on a local machine (such as an email attachment), or delivered by a host on the internet to a local machine.
A large portion of the cybersecurity community’s work goes into fighting phishing and malware. These threats are quite literally the bane of our collective existence. Anything that is even remotely enabling to threat actors is a net negative for the industry.
Old habits die hard
Going back to Google and the unanimous dissent, in a nutshell, the issue is that .zip and .mov have existed for nearly as long as the PC itself as file extensions. In fact, they are ubiquitous file extensions. Every single person with a computer has been conditioned to understand that anything ending in .zip is a folder of files, and anything with a .mov extension is a file containing a movie. To access these types of files, you must click them, and we all know that when anything called ‘kittens.mov’ shows up in your email, you’re clicking it because kittens, right?
The .zip file was brought to market in 1989. The .mov file extension came out in 1991. That’s over 30 years of Pavlovian behavior that Google has weaponized with these new TLDs. Network and endpoint malware detection has become very good. Phishing detection has also improved, but as much as any security solutions have helped, people are more and better-educated on how to spot and avoid clicking URLs that look suspicious.
Is it a file or a domain?
Files and movies (especially those sent from colleagues or friends) are pretty much always going to be clicked. And with these new domains that look like files and movies, threat actors know people will click on their links, regardless of what stuff is on their hosts. (Spoiler alert, it’s not good stuff.) This is what the latest call to arms is all about. These new TLDs are enabling threat actors to subvert decades of ingrained consumer behavior with malicious intent.
This is why cybersecurity professionals are upset. From a security standpoint, there is simply no plausible justification for these specific TLDs to exist. Moreover, when you consider that literally any word in the dictionary can be used to create a TLD, it’s hard to imagine any legitimate, benign use cases for .zip. It simply makes no sense.
All that said, here’s what you can do to protect yourself or your organization from .zip and .mov domains.
How to check the risk of a .zip domain
- Go to www.threatyeti.com
- Type or paste any domain ending in .zip or .mov
- See high-fidelity threat verdict and context including:
Risk Rating
Scored 1 to 10 down to two decimal places for a fine-grained assessment of a domain’s risk. One is safest, ten is riskiest.
Category
Visitless site classification into at least one of 83 categories so you know what’s on a site without risking the visit.
Redirect Chain
See the URL redirect chain and know where it leads. The unassuming link that comes into a client isn’t always the riskier URL where the click ends up.
Related Hosts
See other domains on a host and their risk scores as well. Get the context to understand and take any action on related entities.
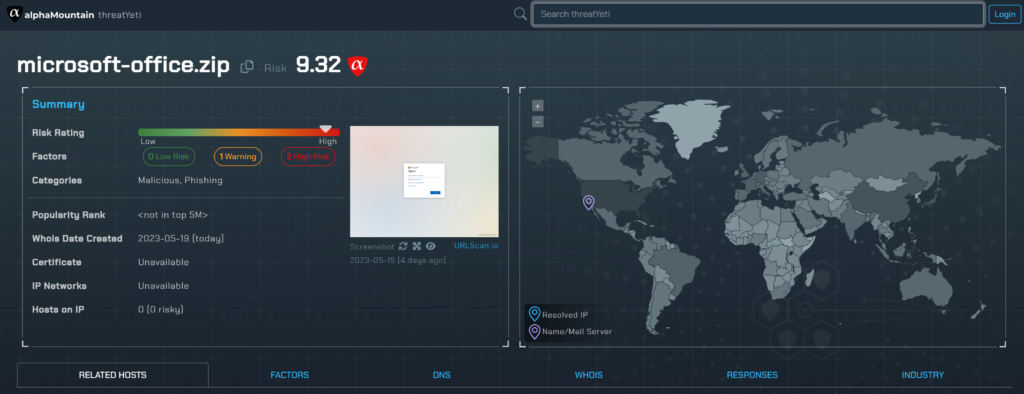
Examples of risky .zip domains
If you find yourself still wondering what the big deal is, or if you need of an example .zip domain to evaluate its risk, just take a look at these recently-created specimens and their risk scores, feel free to copy and paste one into threatYeti, and then ask yourself if you could potentially see yourself clicking on one of these. We already know the answer.
microsoft-office[.]zip 9.32 (threatYeti report) gmailbackup[.]zip 9.29 (threatYeti report) paypal[.]zip 9.26 (threatYeti report) payslip-statement[.]zip 9.24 (threatYeti report) eicar-test-file[.]zip 9.21 (threatYeti report) google-drive[.]zip 9.16 (threatYeti report) e-mails[.]zip 8.64 (threatYeti report) paymentinfo[.]zip 7.64 (threatYeti report) benign[.]zip 7.63 (threatYeti report) porno[.]zip 7.01 (threatYeti report)
That’s it. No one ever said cybersecurity was going to be boring, and these latest TLDs have proven that sometimes we in the information technology industry manage to make life harder on ourselves. But we have to keep going and we have to protect us from both us and them. This is an own goal, and clearly, we now just need everyone to play goalie.