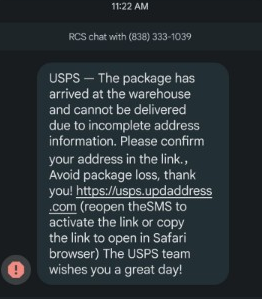
Imagine this. It arrives just like so many other SMS messages these days. It’s from an unknown number, it’s got a call to action, and it’s not overly-threatening. In fact, it’s actually kind of friendly: “Avoid package loss. Thank you!” “The USPS team wishes you a great day!”
The URL itself isn’t a total disaster of alphanumeric domains and weird TLDs, so you don’t reject it out of hand on optics alone; you actually read the URL and it’s intelligible. You are indeed currently waiting on a package.
Could this be legit?
Now, if you’re a follower of ours or a cybersecurity enthusiast, you’ll probably key in on three eyebrow raisers in the message itself. First are the two typos: the double punctuation and the missing space. The third is a bit more subtle, but still suspicious. Why would the USPS ask you to use Safari specifically? Moreover, what’s with the directions on how to click a link? Don’t we all know how to do that? This seems suspiciously prescriptive, and frankly, it probably gives this away as a scam more than anything we’re about to see.
In any case, let’s follow the URL and see where it leads us.
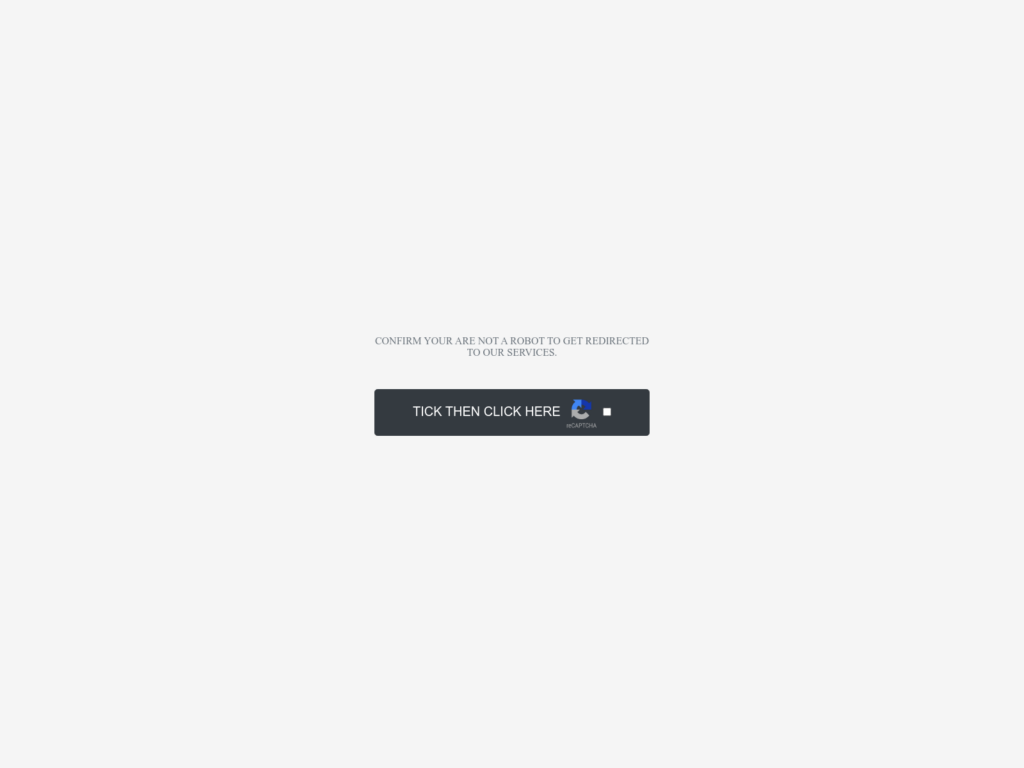
This landing page is a psychological operation. Designed to replicate the authenticity of the well-established Captcha process, this benign landing page builds trust with the user despite its conspicuous challenges in style and word choice. For example, ‘Tick’ is not a word used very often in calls to action.
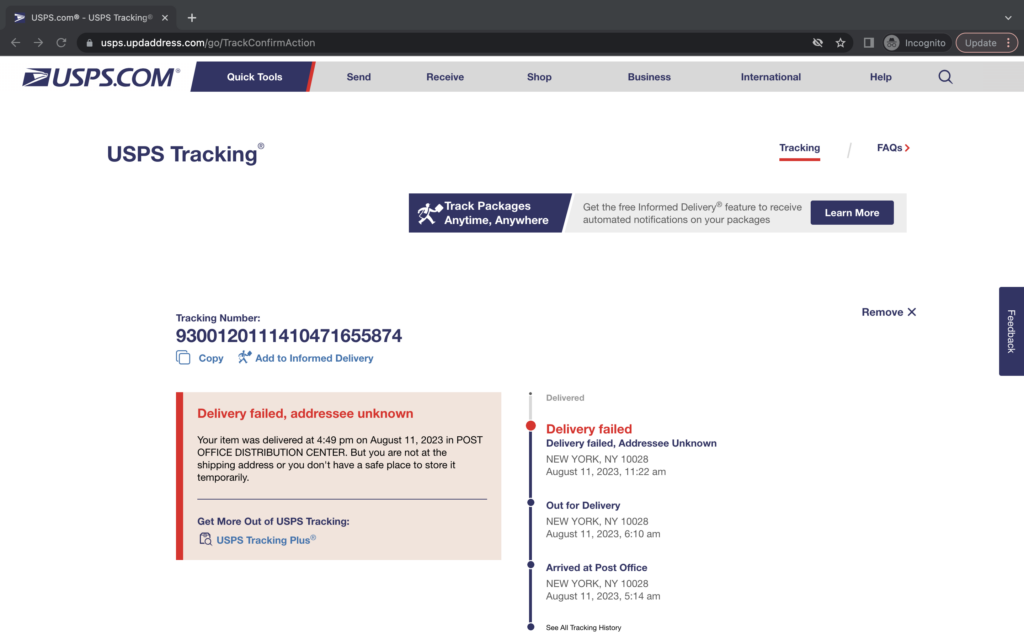
After clicking the dubious Captcha, the victim is taken to a very legitimate-looking USPS-branded package tracking page. And this is where you have to give the perpetrators of this scam some credit.
A very soPHISHticated threat
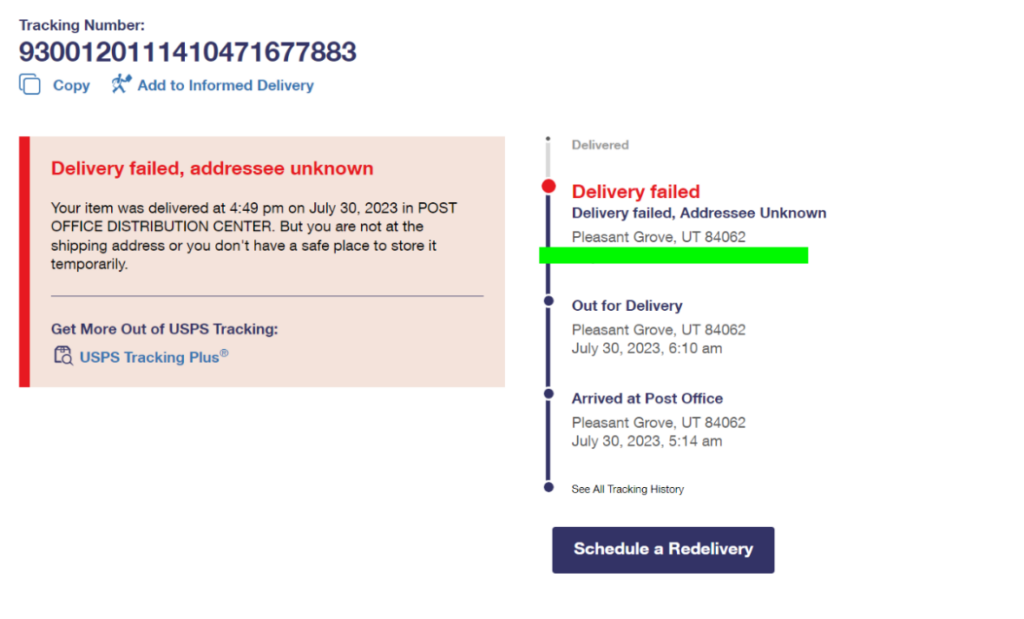
First, the page is a dead ringer for an official USPS page. The css and design elements are clearly lifted directly from USPS.com and the navigation and footer links all point back to the legitimate domain.
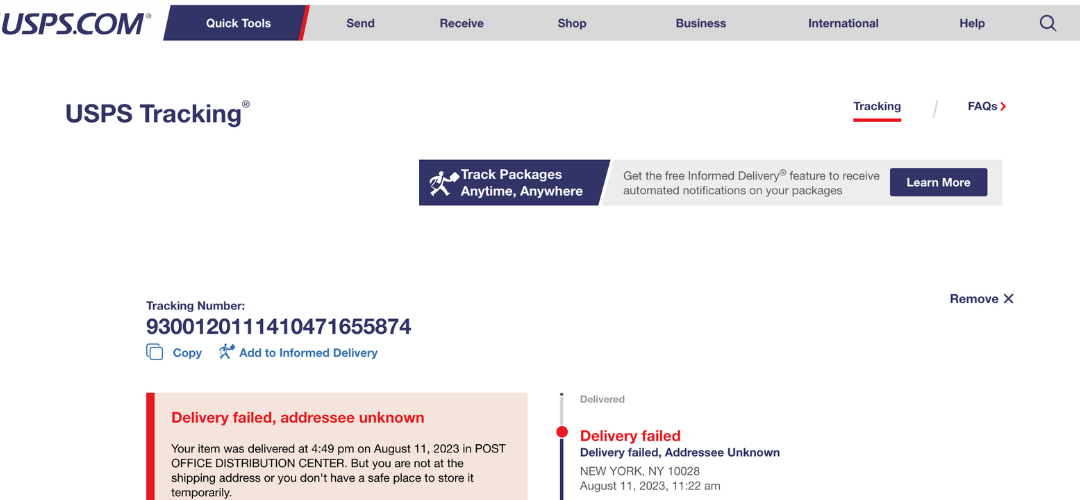
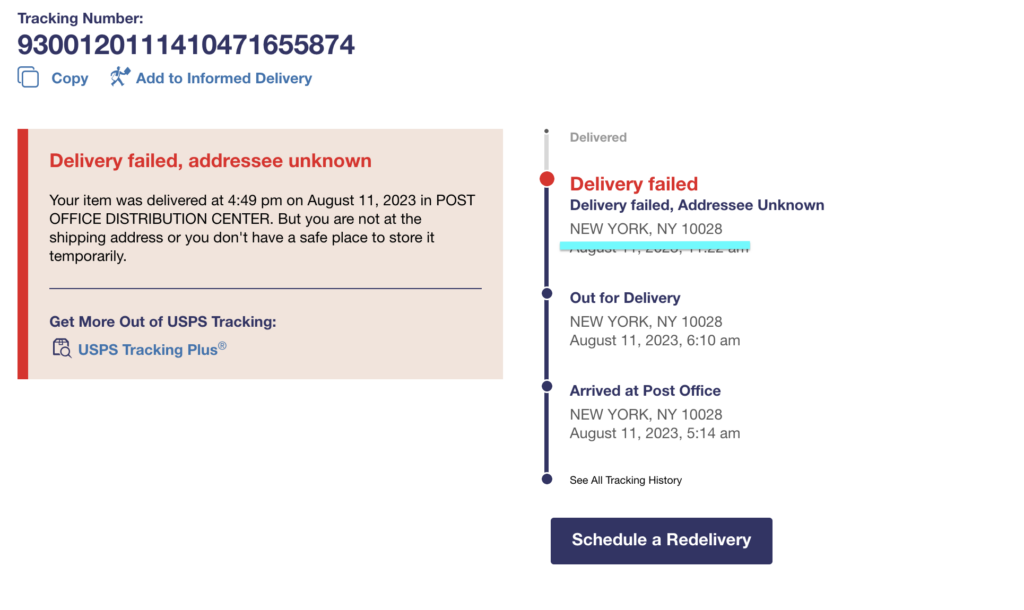
Second, the perpetrators went through the trouble of using the recipient’s actual IP address to resolve a city and state for the delivery failure message. In the example below, the initial page on the left was viewed in a location quite close to the displayed destination. We then tested this from other locations and got locations returned that were of similar proximity to those.
This level of personalization is extraordinarily sophisticated for a threat like this, and it preys upon the victim by giving them confidence that this scam is legitimate. This is top-notch deception.
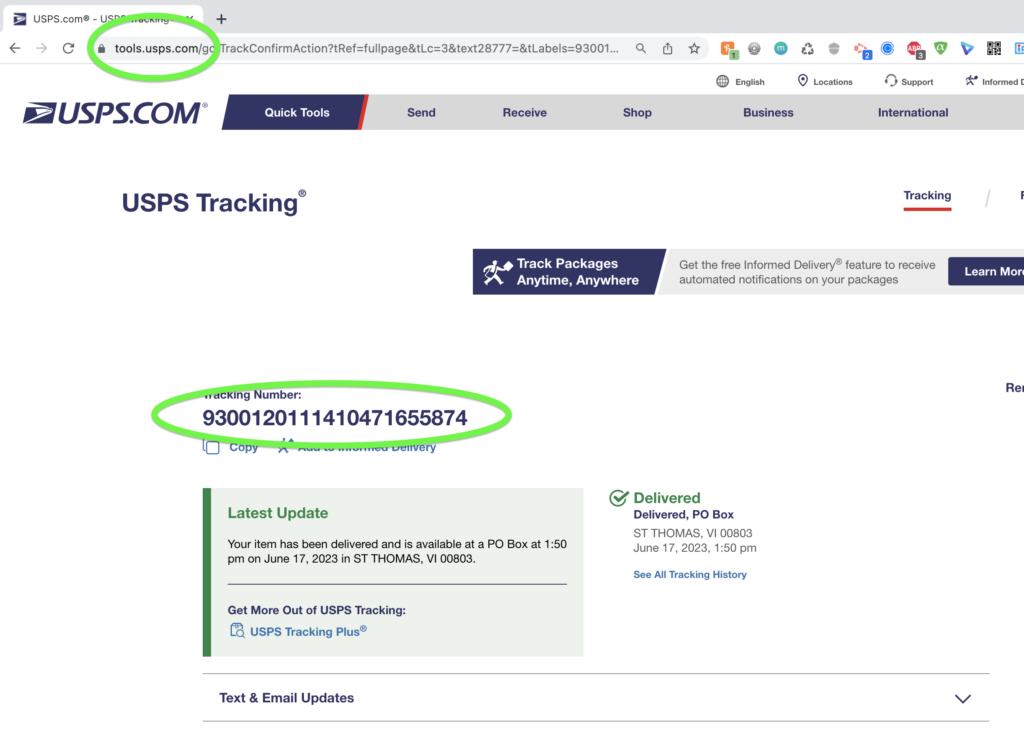
(Sidenote below.) If you copy and paste the tracking number into the legitimate USPS package tracking website, it returns results for a real parcel sent to a totally unrelated destination. Presumably, this USPS tracking syntax is easy to spoof, or the fake site just uses any number of pre-fetched real tracking numbers to dump into this webpage as the victim loads it.
Hooking the phish
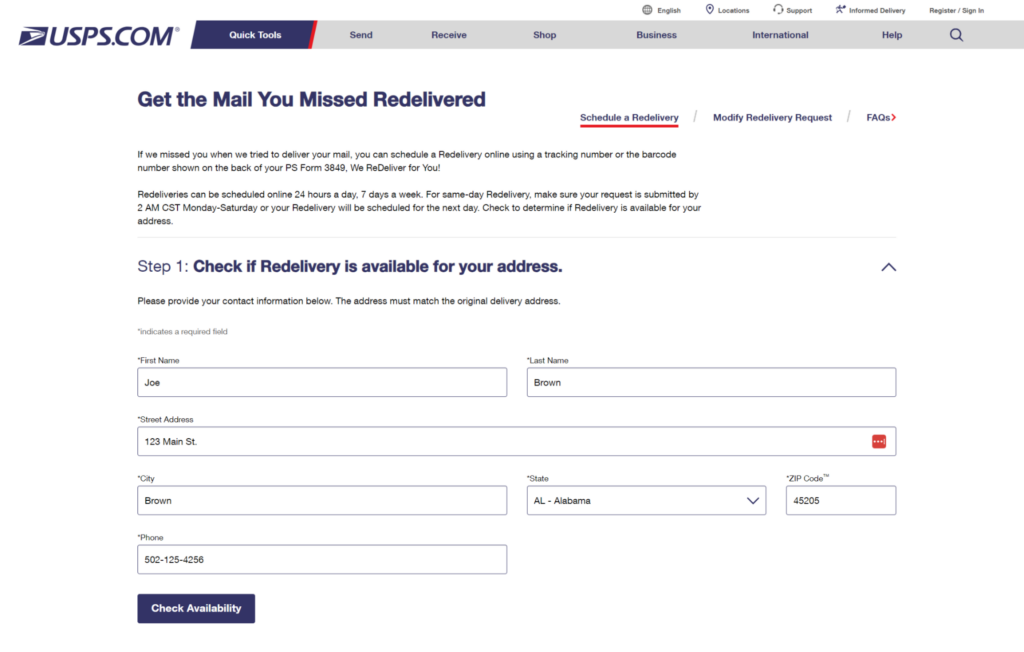
Moving on to the actual crime here, the call to action is a blue button that says “Schedule a Redelivery”. When this is clicked, the victim is taken to a form where they are asked to furnish their address to check if redelivery is available to them. This is again a standard USPS workflow, further increasing its legitimacy in the eyes of the victim.
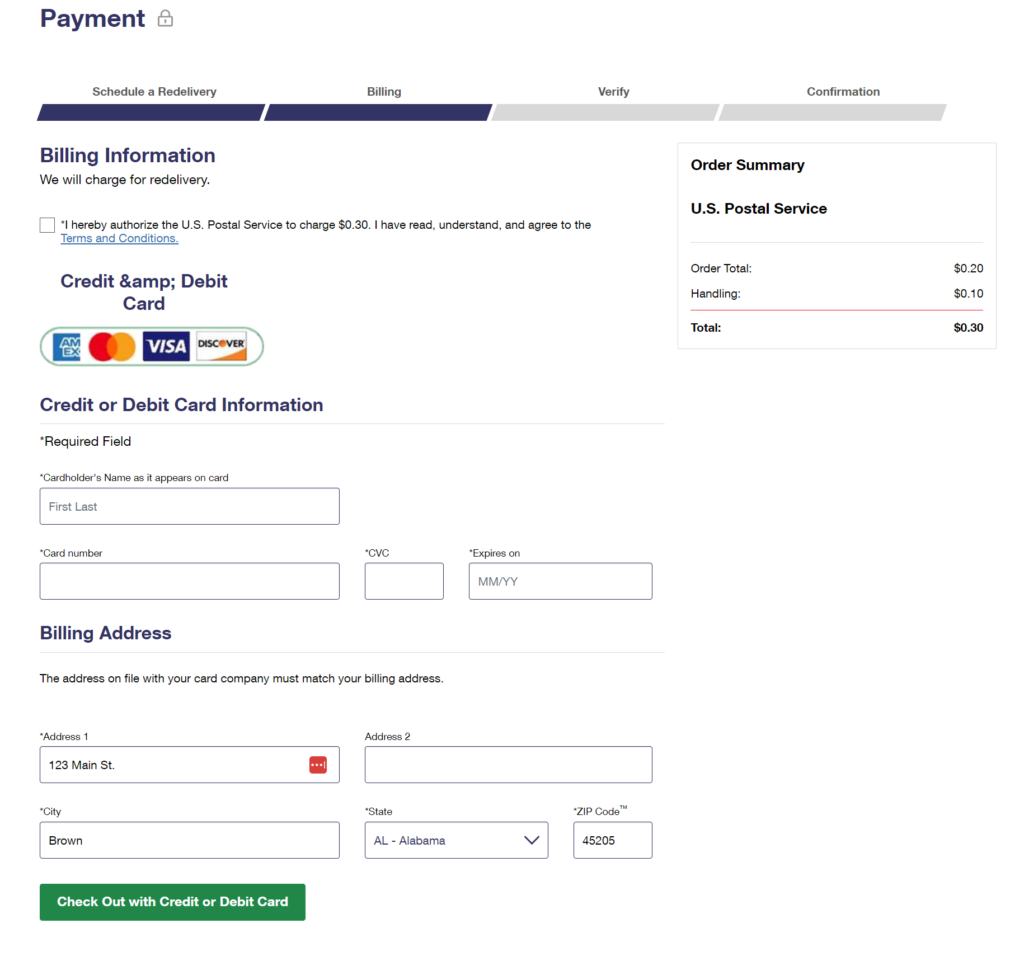
Once an address has been entered, the victim is taken to a credit card form where they are asked to provide their information in order to schedule the redelivery.
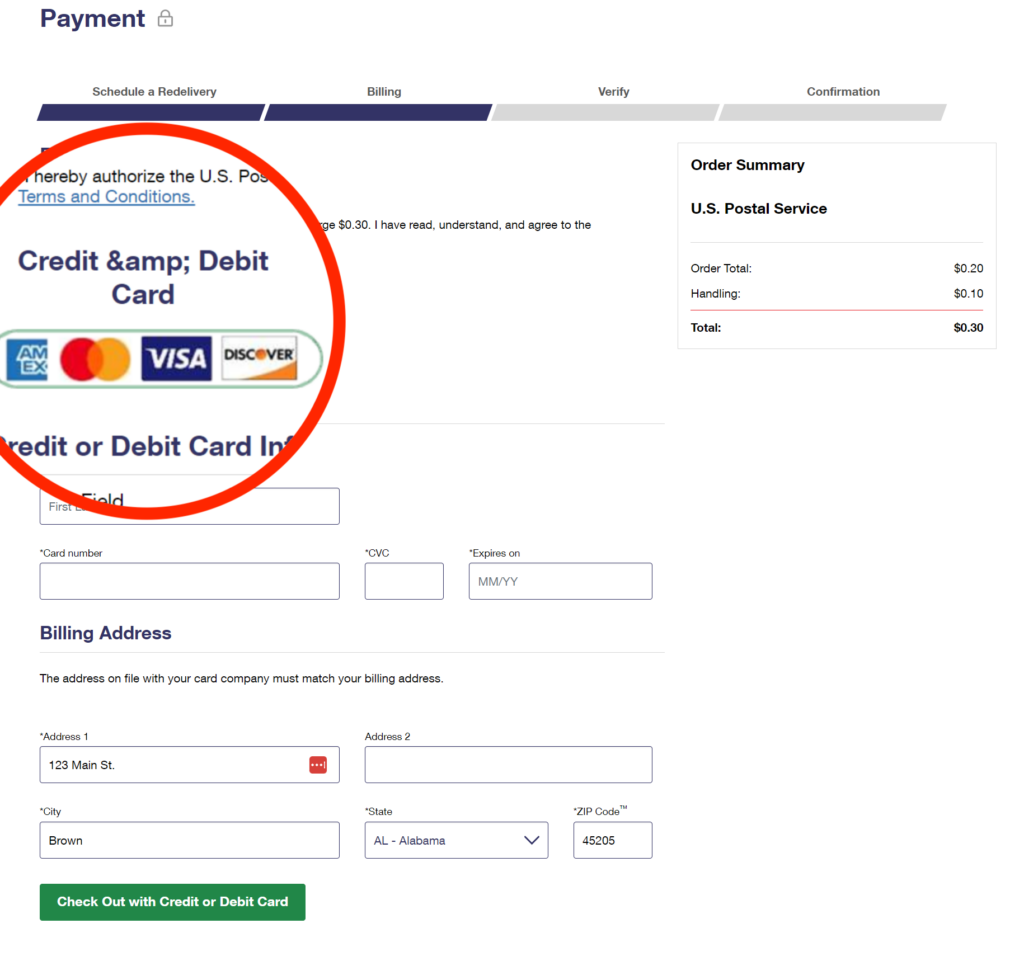
Now, this penultimate page raises some eyebrows for a number of reasons. First, there’s an encoding error in the in the form title which would be very unlikely on an official USPS website. Second, the credit card logo image is quite blurry and, again, not likely to be found in such a state on the official USPS site. Third, the request itself for money or a credit card is not how the USPS conducts business. They occasionally charge a small amount for certain services such as a mail hold, but never for a redelivery such as this.
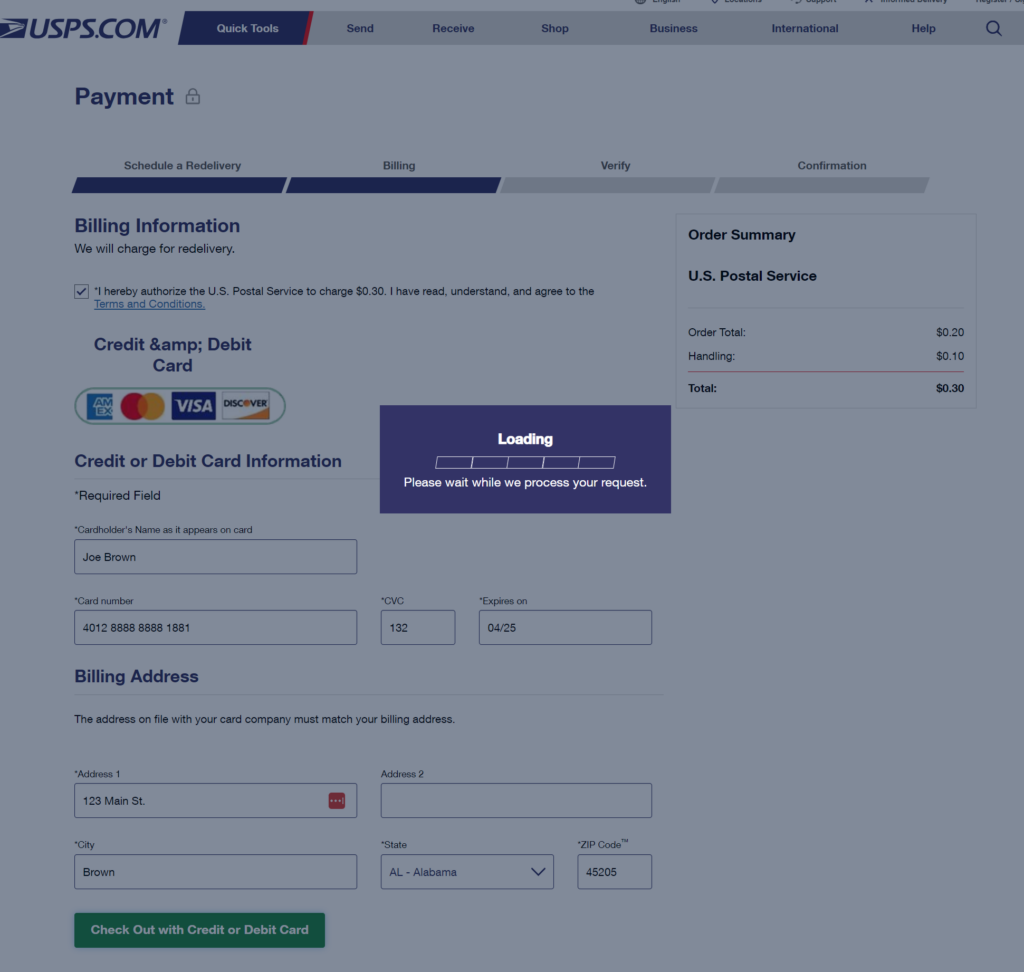
Finally, when the victim enters their credit card information, the damage is done. The webpage just hangs indefinitely on a ‘Loading’ message while the credit card information is passed along to the perpetrators.
At this point the threat actors have the victim’s credit card information to exploit any way they choose. This is a straight up phish, and a very sophisticated one at that.
Detect phishing sites with threatYeti
Now that we’ve seen how this phishing scam is perpetrated, let’s take a second to look up the URL on threatYeti, alphaMountain’s domain threat intelligence platform for threat analysts and security researchers.
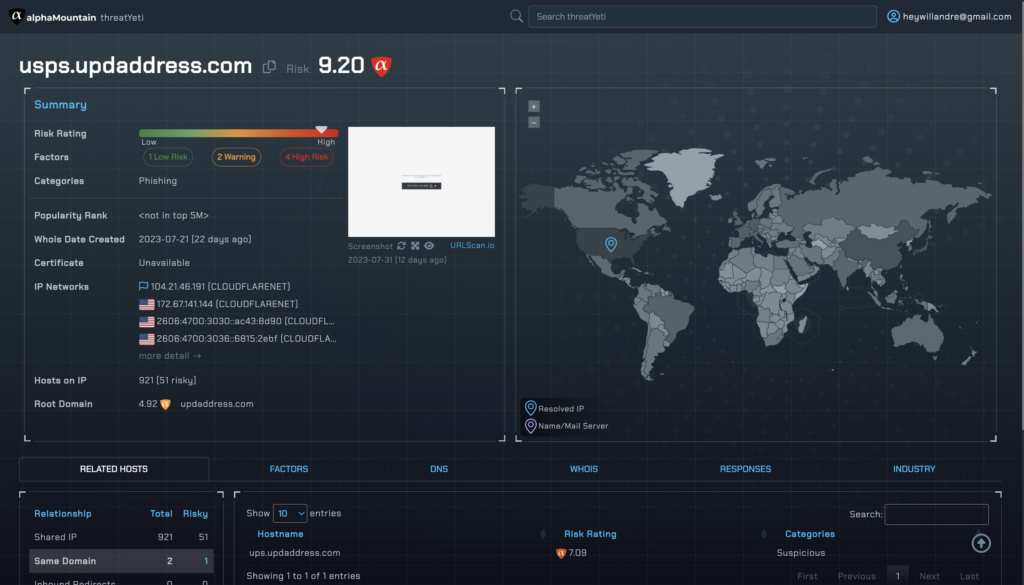
Right away, we see that the site is categorized as a phishing site with a high risk score of 9.20. The screenshot shows the same dubious Captcha page we saw earlier. One of the key differentiators of our data is our Factors which shows you why a domain or IP gets a certain risk score. In this case, we see that the domain has 4 High Risk, 2 Warnings, and 1 Low Risk Factor contributing to this threat verdict.
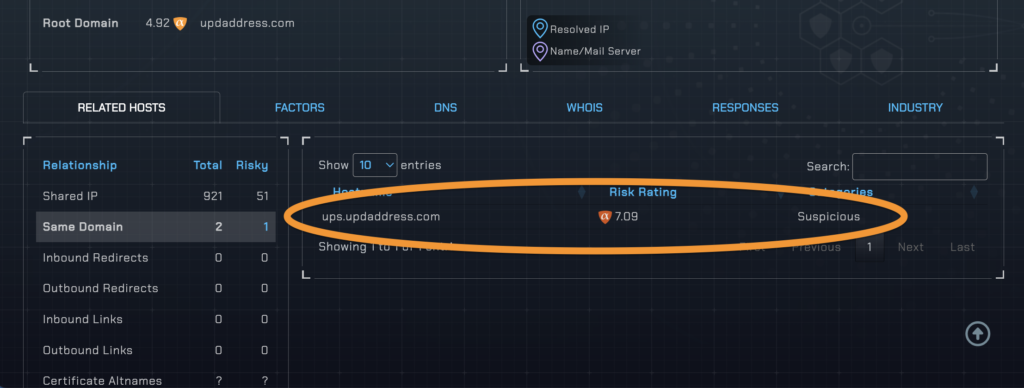
In addition to factors, threatYeti also shows you related hosts. This is useful when conducting an investigation and the scope of threat or threat group needs more context. And, in this case, the one related host is quite interesting.
We see from this information that these perpetrators are not only conducting this scam by impersonating the USPS, but also UPS which is another delivery service with package tracking and redelivery. With this information and given what we’ve already covered regarding steps they’ve taken to make their scam look legitimate, it’s clear that this threat actor has honed their craft by focusing on a theme and using it to exploit victims.
That’s a wrap for this teardown of a USPS phishing scam. Make sure you follow us on Twitter / X and keep up with the latest on IP reputation, web categorization and threat intelligence. Or, request your free trial API key and see how alphaMountain’s domain and IP reputation threat intelligence can make your cybersecurity stronger and faster.