When a post promising a Trader Joe’s gift basket for just $12 began circulating on Facebook, it didn’t take long for thousands of people to click, share, and wonder if the deal was too good to be true. According to a recent Snopes investigation, it was exactly that: a carefully orchestrated scam designed to harvest personal information under the guise of generosity from a beloved grocery chain.
The post claimed that anyone over 50 could claim a basket of Trader Joe’s goods by completing a simple online form. But as Snopes made clear, Trader Joe’s does not sell online and has never offered digital coupons or giveaways.
The URL tied to the scheme — food-basket[.]org/traderjoes — wasn’t connected to the retailer at all. Instead, it was a phishing site dressed up with Trader Joe’s branding, urgent countdown timers, and survey questions, all intended to push unsuspecting users into surrendering personal and payment details.
threatYeti: The Free Malicious URL Checker
This is where threatYeti, alphaMountain’s malicious URL checker, proved it’s worth its weight in chocolate. Some security tools and crowdsourced databases might have taken hours or days to flag the link as dangerous. In fact, as of this writing, alphaMountain is the only threat intelligence provider to have correctly identified the URL as malicious. Since threatYeti runs on the alphaMountain threat intelligence API, it immediately identified it as high risk.
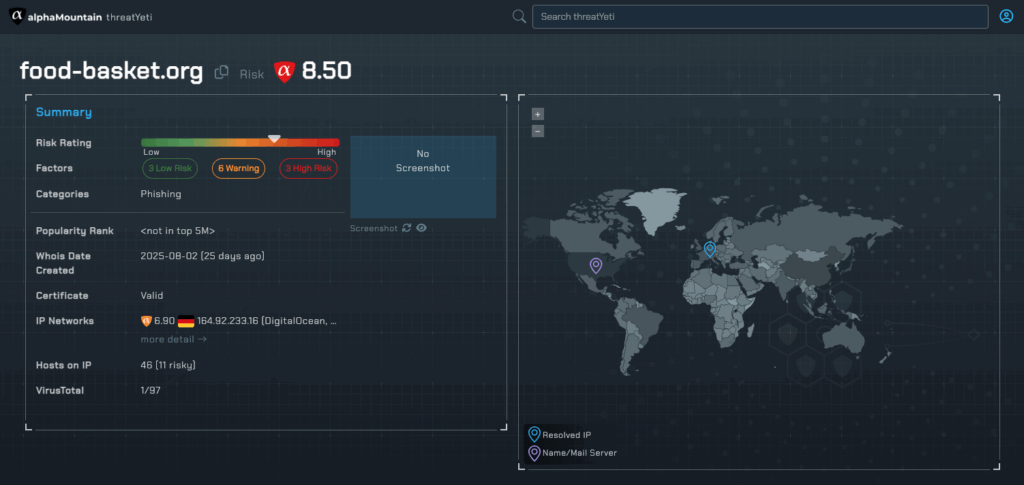
The platform detected classic phishing tactics: a newly registered domain, hosting patterns linked to other suspicious sites, and classic forwarding behavior, where the site displayed a different final URL from its initial link. By catching these deceptive signals in real time, threatYeti provided the kind of decisive verdict that stops scams before they spread further.
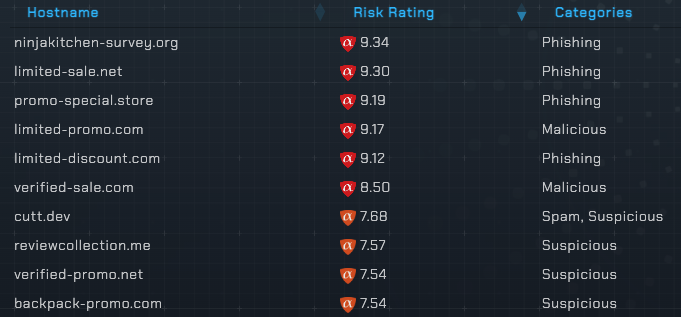
A deeper look at the hosts related to the original domain reveals dozens of additional risky domains using deceptive words such as “survey”, “promo”, “discount” and “sale”.
What this incident illustrates is that the stakes are higher than ever for URL security. Cybercriminals are adept at exploiting the public’s trust in well-known brands, and their campaigns often appear and vanish in a matter of hours.
A malicious URL checker that relies only on static reputation scores or user reports simply can’t keep up. Real protection requires deep analysis, instant categorization, and the ability to see through tricks like forwarding or urgency tactics.
The Trader Joe’s scam highlights why businesses and security teams need tools that move as fast as the attackers. With threatYeti, the difference is clear: phishing domains aren’t just detected. They’re exposed before unsuspecting customers hand over their information. Snopes did the important work of alerting the public, but threatYeti ensured the URL itself was flagged from the start.
For organizations serious about protecting their users and their brands, the lesson is simple. If you’re still relying on outdated methods to spot scams, you’re leaving the door open. The next time a fraudulent giveaway or too-good-to-be-true coupon makes the rounds, the only thing standing between your customers and a data breach may be the speed and intelligence of your malicious URL detection. With threatYeti, that detection is just a click away.

