Level up your hunting and research with real-time threat intelligence for any host on the internet.
The alphaMountain team is excited to announce the release of threatYeti, our new platform for real-time domain intelligence. Now in public beta, threatYeti is built on top of alphaMountain’s leading security data APIs and is available for free at https://threatYeti.com.
The need for domain intelligence has never been greater. Phishing, scams, spearphishing, typosquatting, and smishing threats continue to increase and evade detection. Whether you’re an independent security researcher or threat analyst inside a well-funded SOC, you’ll find easy access to fast, comprehensive threat verdicts on threatYeti.
When we benchmarked our security data API against recognized domain intelligence tools, we knew right away that we needed to develop a browser-based solution to give analysts of all skill levels access to our data. We continue to outperform the household names in this space, so we are really excited about making alphaMountain’s fresh data and threat verdicts accessible to more researchers and analysts.
Here are a few capabilities of threatYeti that we are really excited about.
Threat Rating
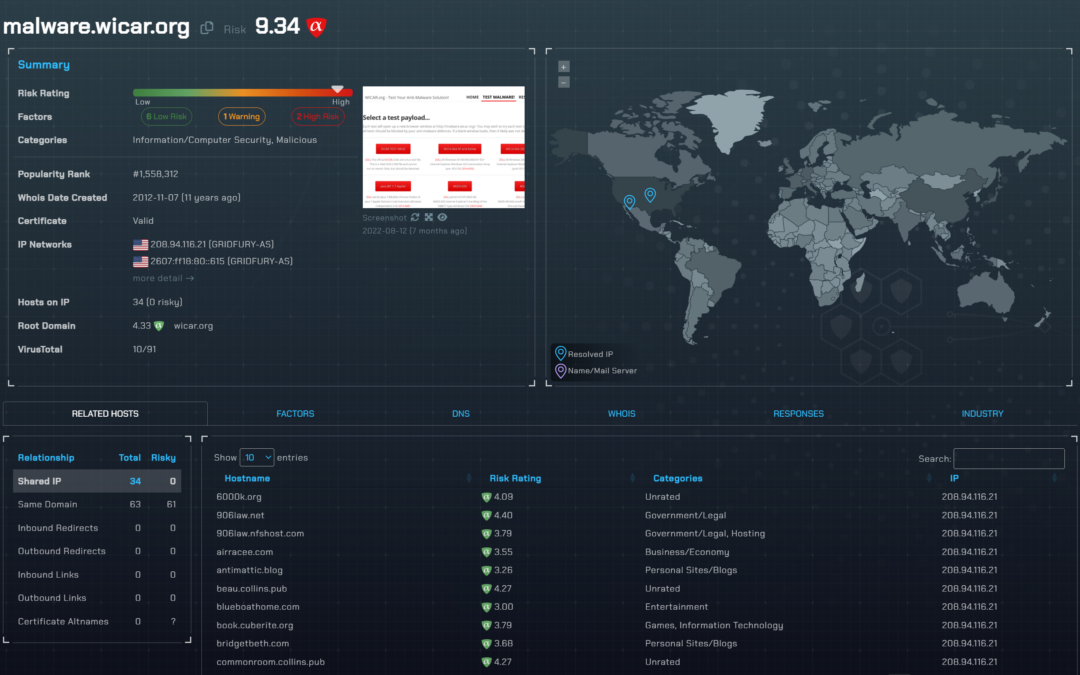
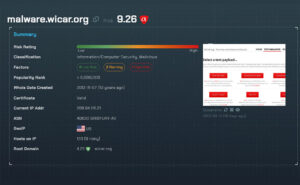 We give you a simple color-coded threat score of any host you search. This takes the guesswork out of assessing the risk of any domain and it helps you move faster to report or act on these domains. We also show you the factors that go into the rating, so if you’re currently using any SIEM rules or homebrewed algorithms to assess the risk of a domain, you can use our threat rating and factors as a quality check for those.
We give you a simple color-coded threat score of any host you search. This takes the guesswork out of assessing the risk of any domain and it helps you move faster to report or act on these domains. We also show you the factors that go into the rating, so if you’re currently using any SIEM rules or homebrewed algorithms to assess the risk of a domain, you can use our threat rating and factors as a quality check for those.
Categorization
We categorize every host into one of 83 categories. This means that you don’t need to visit risky sites to know what they’re all about. Categories include visual and textual content, as well as risk categories like “Suspicious”, “Phishing”, and “Malicious” designations.
Related Hosts
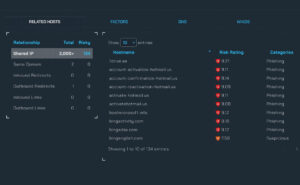 Context is king in any threat investigation, so we present every host related to whatever you’ve searched. As the saying goes, “where there’s smoke, there’s fire,” and seeing related hosts (along with their own categories and threat ratings) gives analysts and researchers the leg up in uncovering scaled, distributed or deceptive operators.
Context is king in any threat investigation, so we present every host related to whatever you’ve searched. As the saying goes, “where there’s smoke, there’s fire,” and seeing related hosts (along with their own categories and threat ratings) gives analysts and researchers the leg up in uncovering scaled, distributed or deceptive operators.
We have a ton of additional features and capabilities such as integrations, certificate scans, screenshots and more to come. You can read about some of those on our edition comparison here.
Try threatYeti for free
The best way to explore threatYet is to just dive in for yourself right away. You can access threatYeti for free with no account. If you want additional queries and data, you’ll just need to create a free account. To get started, visit the link below and come ready with a link or two that you want to assess. We’re well on our way to a billion hosts scanned – help us get there!