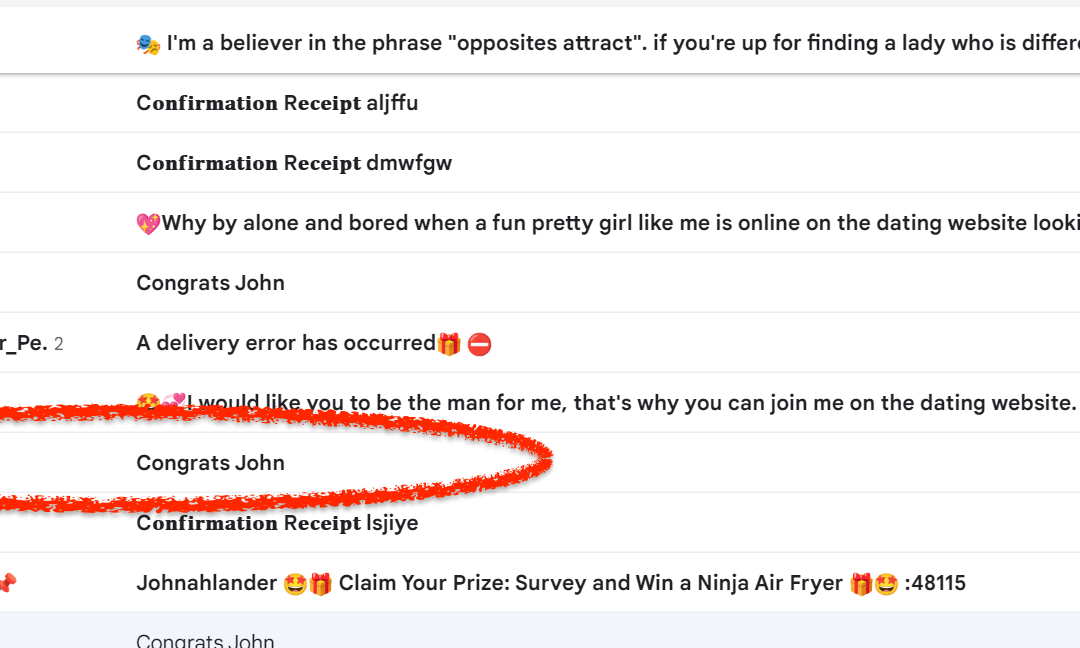
We’re off on another Spam Safari, and let’s just start off by saying that we basically had a Choose Your Own Adventure-level of options waiting for us this month. Our inbox (well, Spam folder, mostly) was absolutely inundated with all sorts of interesting opportunities to be exploited. We had:
- Romance scams
- “Accidental order” scams
- Delivery error scams
- Survey reward scams
We decided to investigate an offer that seemed quite reasonable and right in line with the amount of money we were prepared to part with in order to bring you, our reader, this scintillating tale of intrigue and suspense. Thus, rather than take up the offer to get a free quote on an extended auto warranty, or some free tools, we opted for a $2 annual subscription to the TV streaming service, Hulu.
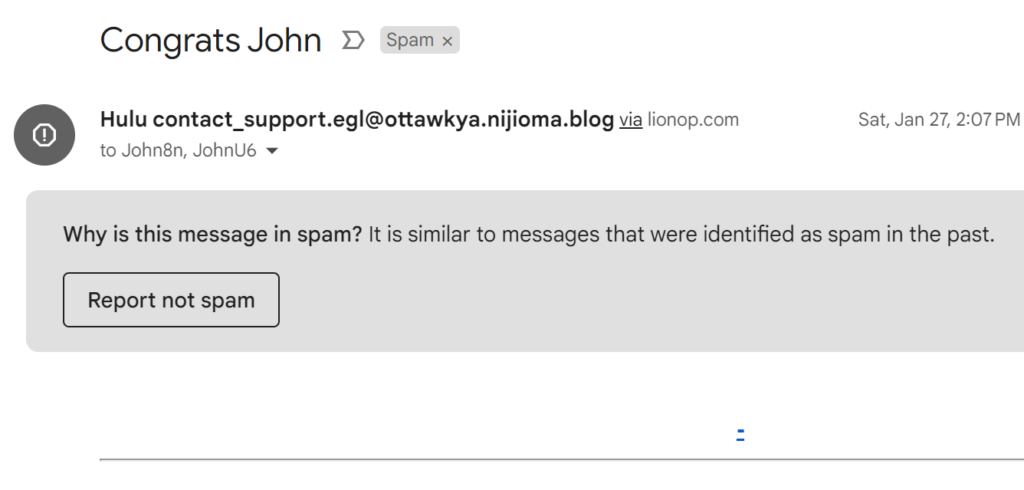
As mentioned, there were dozens of spam emails waiting for us in the Spam folder this month, and they all looked like this, vacant of any real content. Because it was flagged as spam, the mail client (Gmail, in this case) automatically removed the potentially-harmful content, so to get to the image we have to dig into the original message.
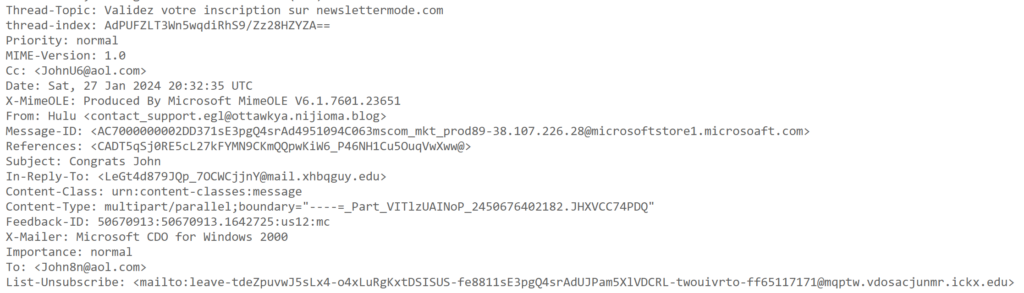
Headers:
The image itself is the entirety of the user-viewable email content. Naturally, it’s linked to a campaign which we’ll explore shortly.
As a quick side note, although hidden, the body of the email actually contains a ton of arbitrary text stuffed in it to throw off spam detectors. A few snippets:
=============
Your subscription to our list has been confirmed.
Thank you for subscribing!
+19147140178
AUTORISATION D’INSCRIPTION
POUR ETUDIANT MINEUR
<p>Thanks for joining the 529 Garage.</p>
<p>Your 529 Garage user name is:</p>
<p>Now, setup a password to complete your signup</p>
—-RW;vahy;oxe
<p>Your Marvel Account Passcode</p>
<p>Here is your one-time Marvel Account Passcode:</p>
<p>573321</p>
<p>Note that this code can only be used once and will expire in 15 minutes. If you did not request a passcode, or if you’ve already signed into the account using another method, simply ignore this message and nothing will be changed.</p>
<p>Code de passe de votre compte Disney</p>
<p>Bonjour arsalan ! Voici votre code de compte Disney à usage unique : 700237 Notez que ce code ne peut être utilisé qu’une fois et qu’il expirera dans 15 minutes. Si vous n’avez pas demandé de code, ou si vous vous êtes déjà connecté au compte avec une autre méthode, ignorez simplement ce message : aucune modification ne sera apportée.
These evasion tactics clearly didn’t work as the email was ultimately relegated to the Spam folder, so chalk one up to the good guys for not falling for these malicious attempts to subvert their controls.
Now, back to the image and the offer for the $2 annual subscription to Hulu, we’ll now follow the redirect chain that this image kicks off when clicked.
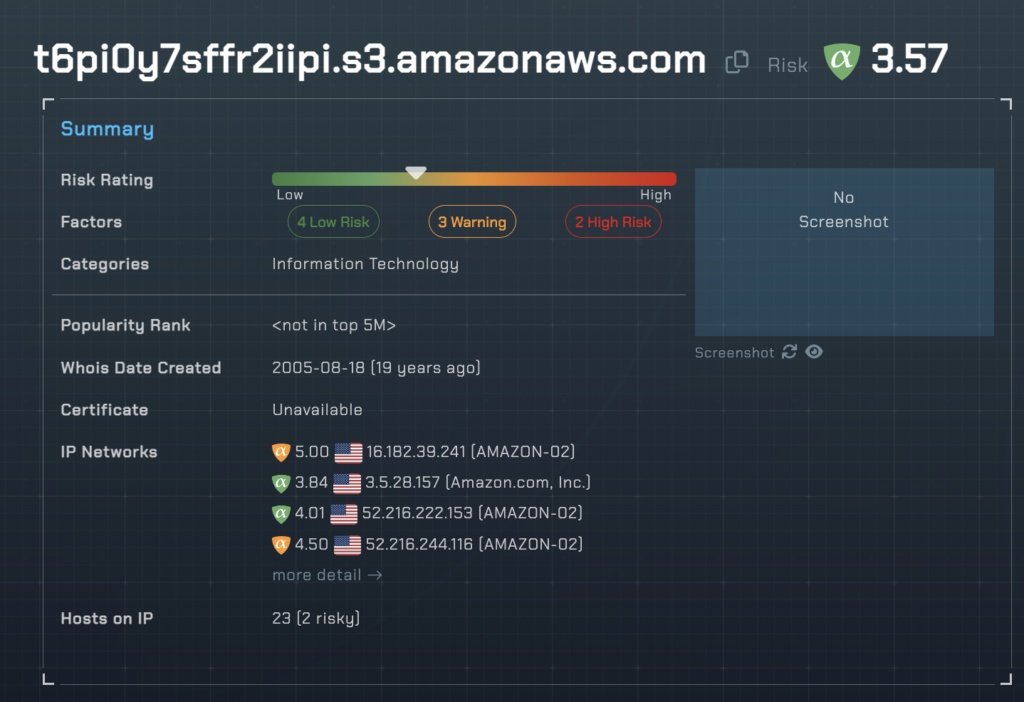
At this stage, we will also show you the threat rating and category of each host in the chain from our domain and IP investigation platform, threatYeti.
https://t6pi0y7sffr2iipi[.]s3.amazonaws.com/t6pi0y7sffr2iipi.html#XWzDWrz:6N:34EKIJG:AEOCH:19125L:2ON3:0:2ON3:0:2H:7M:B:2JJ:2K0:HJOM:83
Following that, it executes the redirect chain.
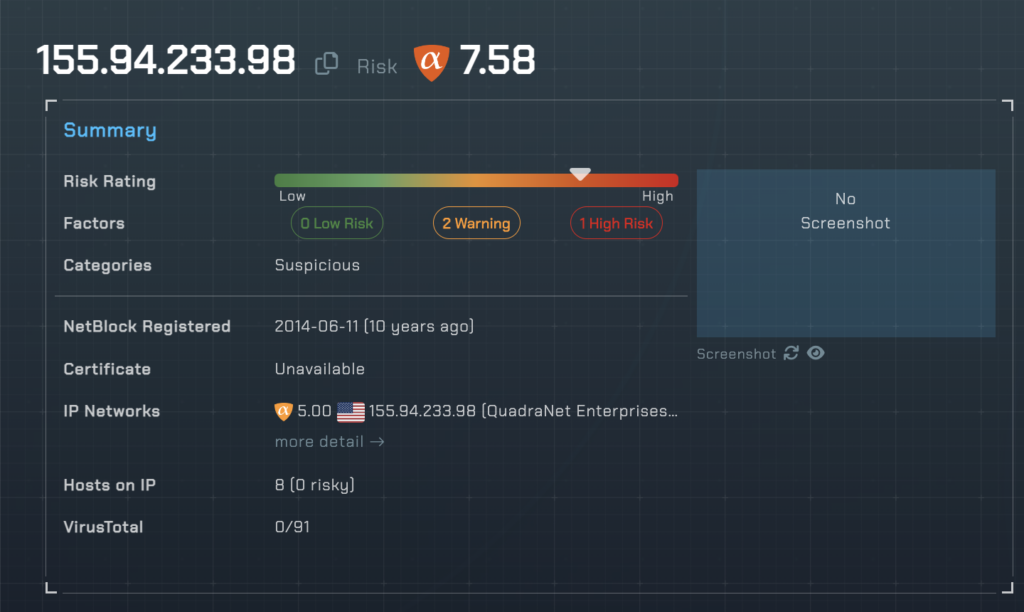
http://155[.]94.233.98/XWzDWrz:6N:34EKIJG:AEOCH:19125L:2ON3:0:2ON3:0:2H:7M:B:2JJ:2K0:HJOM:83
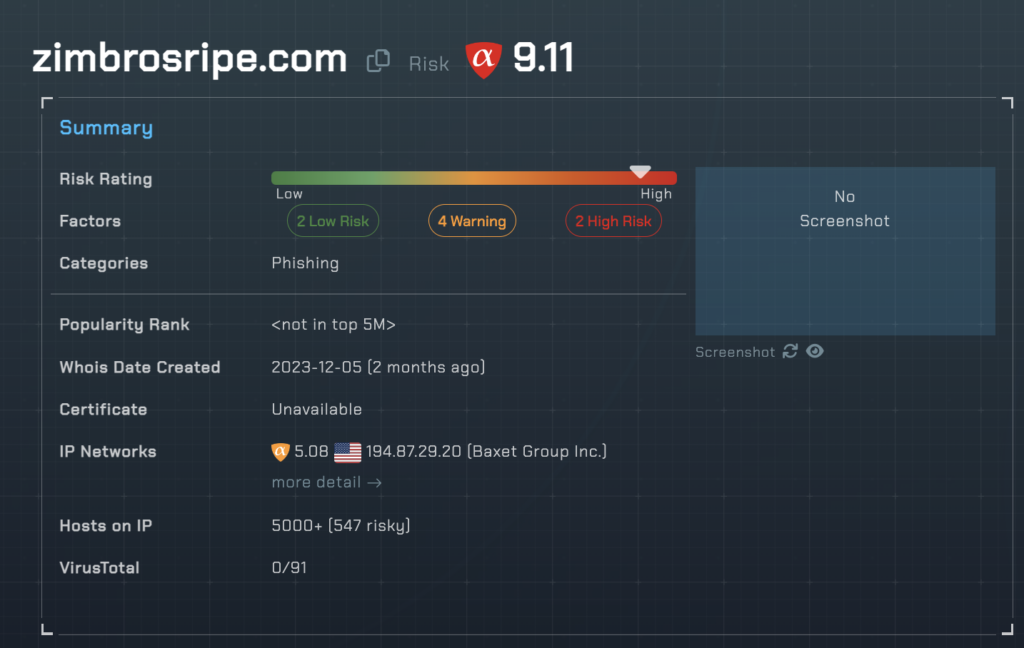
https://zimbrosripe[.]com/0/0/0/54f5be44bc9e6f704fe5288ef12ecbde/51977_16013239_11_1872_69/xRYvhvkXwtaJKaZsprRWYcpwZFIngtPEhHWjxIEghfbNNIoZGJwbAgAKpQbbpRDTr/69
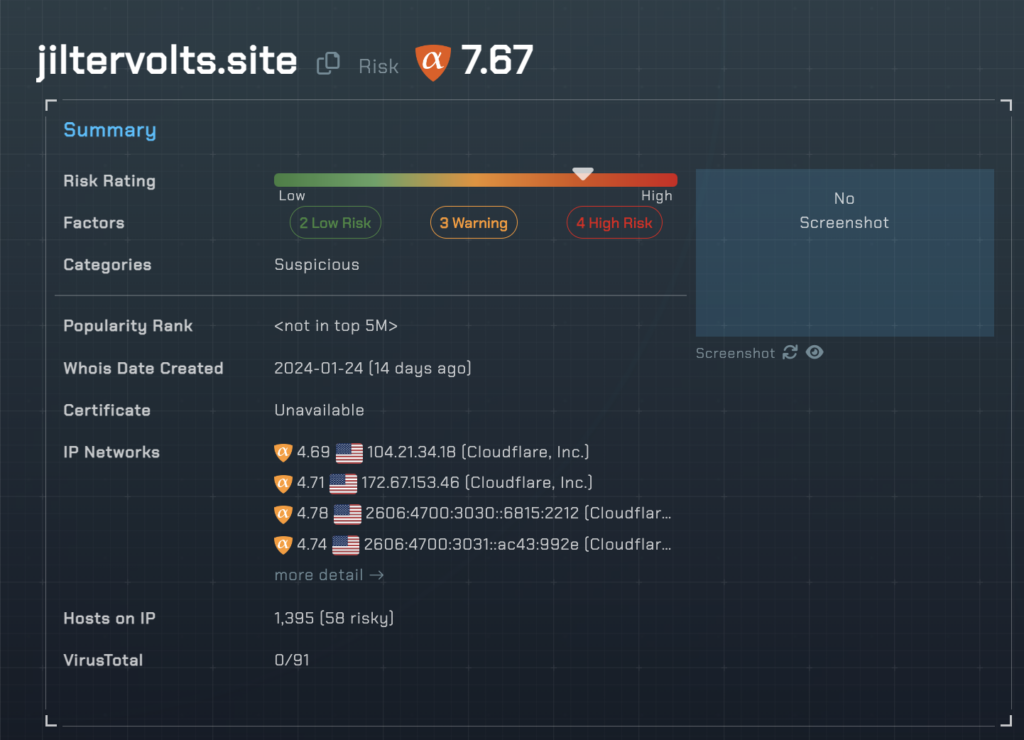
https://jiltervolts[.]site/?s1=350609&s2=1134958386&s3=6275&s10=3938
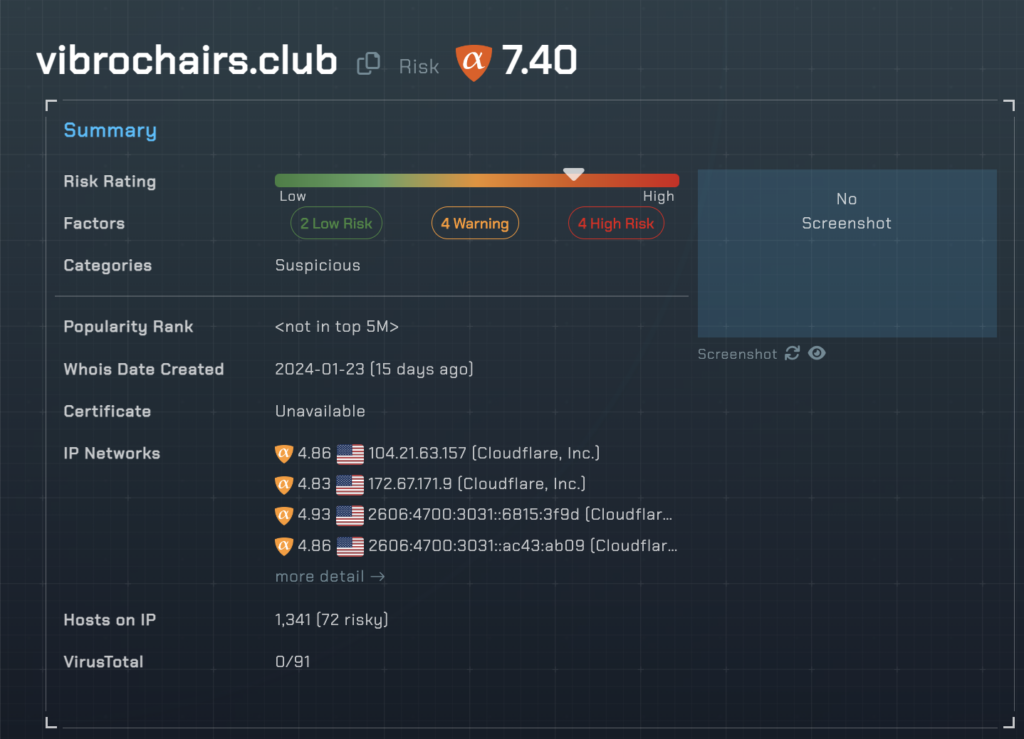
https://vibrochairs[.]club/36f916242f8cebcc861c0a0f5f7767e5
Like the junk text in the email body, these redirects are designed to evade security measures.
It’s worth noting that a firewall or other network security device with the proper URL filtering capabilities and thresholds in place would stop this scam in its tracks.
For example, that “zimbiosripe” URL above pegging a 9.11 risk score from alphaMountain would be blocked with a risk threshold of 9 or greater on the firewall, and the end user would simply never reach the threat actor’s goals for this campaign. Naturally, we recommend a far more conservative threshold of around 7 with our security partners so that their end users are further insulated from malicious URLs.
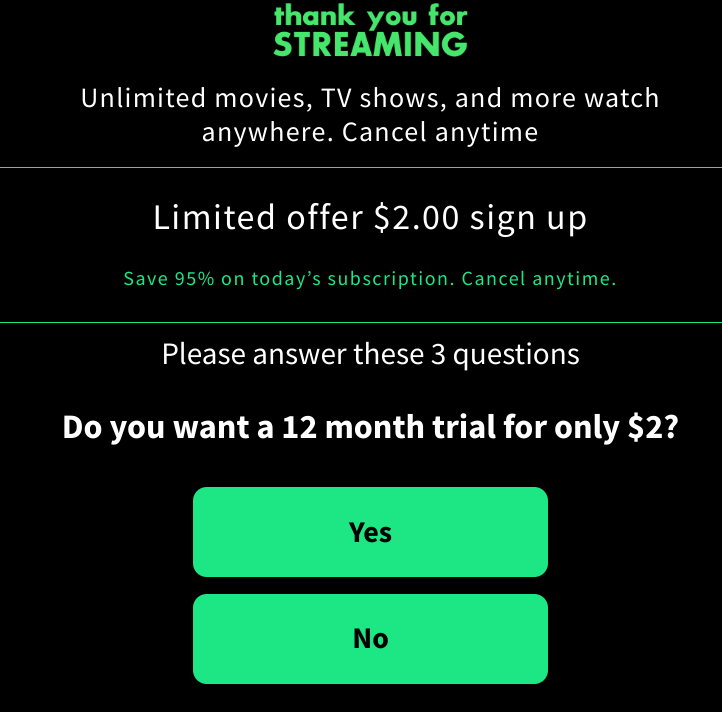
We finally arrive at the first screen where the user can take any action, and it’s this short quiz. Notably, the text says “Please answer these 3 questions”, but when you click ‘Yes’, the user is immediately redirected several times to a payment page.
It’s also worth noting that this redirect chain is dynamic. The links in the chain changed between the first and second time we followed the prompt above. This is yet another evasion tactic.
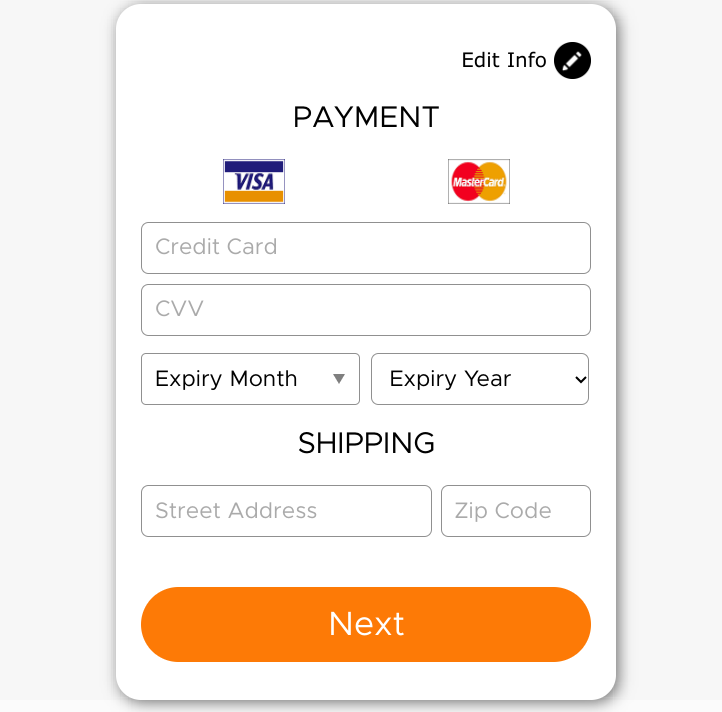
Nevertheless, we end up at this payment form.
After entering valid payment information, the charge was declined–several times. This was due to a $10 maximum daily rate for the card and the $12.95–not the $2 advertised! In the words of the great Julius Caesar, “Hath thy hackers no shame?” Interestingly, each of these transactions was attempted on the payment gateway by a different entity. Again, these are evasion tactics to avoid detection of the scam at the banks and payment processors.
Interestingly, after increasing the credit card limit on our side, we retried the card and it was declined again. However, this was not a real charge attempt. The threat actors are using an intermediate gateway to present a declination message in the browser, but there was no actual declination at the bank. Presumably, this is to prevent multiple fraud attempts from ever reaching the bank and potentially tipping them off to their scam. Sneaky!
We decided to swap credit cards and start over, this time with a limit of $15. With our new limit (and after enduring the aforementioned, new redirect chain to the payment gateway), we found success and our transaction was completed. But, wait! This time it was for $9.95. This change from the previous amount would again suggest detection evasion by the threat actors in the face of a fraud investigator at a bank. By moving the amounts around, they would be harder to detect at scale.
Success!
So, with that, the threat actors are now in possession of our $9.95, but it wasn’t all in vain. We’re now a part of the club! Granted, you can’t do anything here other than call a toll-free number to speak to a “customer service” representative, but, hey, what’s a safari without a few animals?