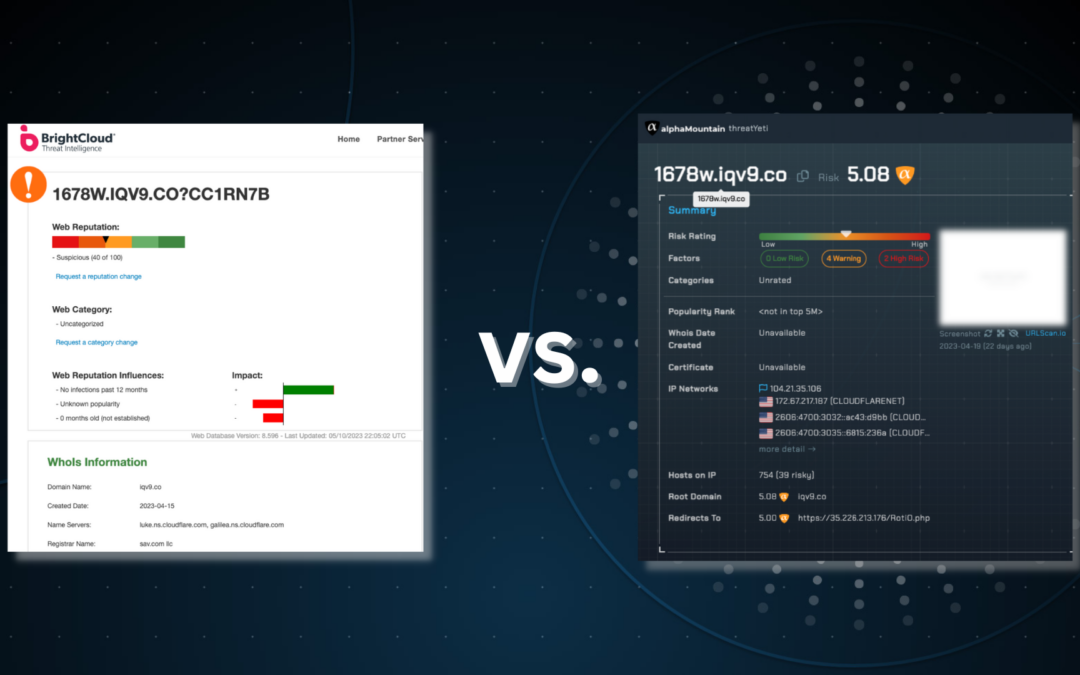
From time to time we like to test different IP reputation and web classification solutions, and what better way than by taking the most recent SMS spam message from your mobile phone (you know you’ve gotten one recently) and putting the URL into different solutions to compare their results.
BrightCloud URL lookup is a well-known IP reputation solution from OpenText Webroot. They offer a number of API services to help organizations determine the risk or classification of hosts on the internet. (Spoiler alert: that’s what we do, too.) Like us, they also offer a web-based URL analysis solution, but that’s about where the similarities end.
Initial Thoughts
Truth be told, it’s a little challenging to assess the quality of BrightCloud’s Threat Intelligence Services. Their free solution called “URL or IP Lookup” doesn’t return a whole lot of information for any given query, so it’s hard to know what intelligence they actually possess about a domain or IP address.
That said, let’s dig into a short comparison of BrightCloud’s free URL or IP Lookup to alphaMountain’s free version of threatYeti domain threat intelligence platform and see what each one tells us.
We received the following message via SMS on April 18, 2023
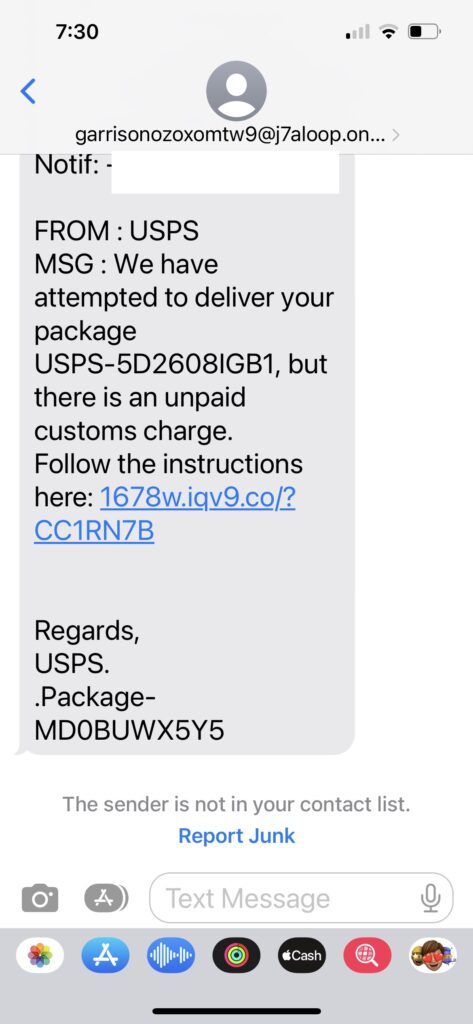
1678w.iqv9[.]co?CC1RN7B is obviously a dubious URL, so that’s what we’ve put into both BrightCloud and alphaMountain to see what we can learn.
| BrightCloud | alphaMountain | |
| Solution | URL or IP Lookup | threatYeti |
| Version | FREE | FREE |
| Target | 1678w.iqv9.co?CC1RN7B | |
| Lookup Date | 5/9/23 | |
| Received Date | 4/18/23 | |
| REPUTATION | 40/100 (Suspicious) | 5.19/10 |
| CATEGORIES | Uncategorized | Unrated |
| FACTORS SHOWN | 3 | 6 |
| RELATED HOSTS | X | 780 (Risky=39) |
| DNS | luke.ns.cloudflare.com, galilea.ns.cloudflare.com | us 172.67.217.187 (CLOUDFLARENET)
us 2606:4700:3032::ac43:d9bb (CLOUDFLARENET) us 2606:4700:3035::6815:236a (CLOUDFLARENET) |
| WHOIS | Registrar Name | Registrar Name, Dates + Raw |
| CERTIFICATE | Not Offered | Unavailable |
| REDIRECTS TO | Not Offered | https://35.226.213.176/RotiO.php |
Reputation
BrightCloud URL lookup uses a five-tiered ranking system for every domain it ranks. From the upper quintile down (100 to 81) it goes counterintuitively in order of most to least “safe” with Trustworthy at the highest end, to Low Risk, Moderate Risk, Suspicious, and High Risk at the lowest end of the numerical ratings buckets. A five-part color code is present for each quintile from red to green. For what it’s worth, every URL we have put through this BrightCloud tool lands on a multiple of ten which renders the value of a three-digit scale to be rather dubious.
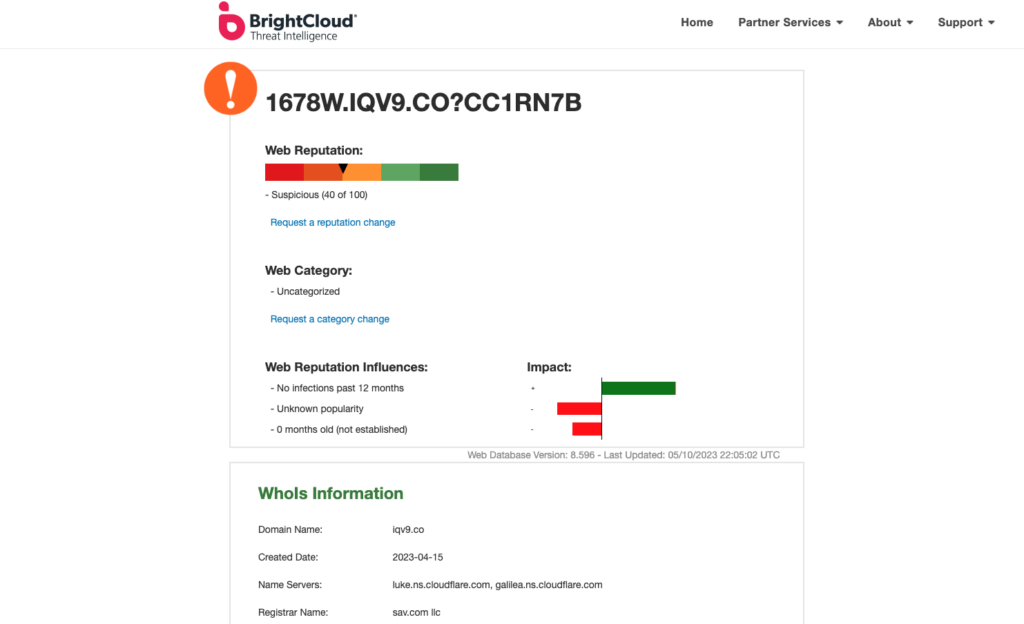
BrightCloud URL or IP Lookup results page
alphaMountain provides a threat ‘Rating’ scale from 1 to 10 and down to two decimal places, with ten being the riskiest and one being the safest. A three-part color code of green, orange or red supports rapid cognition of a domain or IP’s general risk rating.
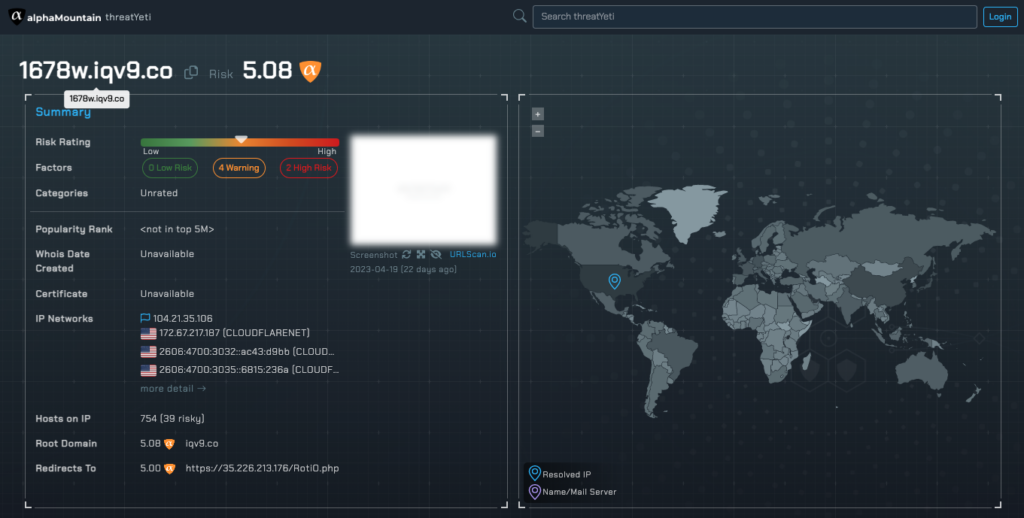
threatYeti domain research platform results page
In the case of this specific URL, BrightCloud gives it a ‘Suspicious’ rating of 40, with a color code on the line between orange and yellow, and alphaMountain gives it a risk ‘Rating’ of 5.08 and color code of orange.
Categories
Both BrightCloud and alphaMountain offer classification of domains and IPs. This means that they will explain the content of the site with ‘Category’ or ‘Categories’ tags that help threat investigators understand the nature of a site without having to visit it. This classification saves time for the analyst and lowers the risk to an organization and its people by eliminating the potential for offensive content to be seen by the analyst, or for harmful software (such as malware) to be dropped onto a machine.
BrightCloud offers 82 content categories (found here) whereas alphaMountain offers 83 (found here). It’s worth noting that despite their proximity in quantity, the categories themselves are in some cases quite different. If you are choosing a threat intelligence provider, you might want to consider reviewing these lists as part of your evaluation as you might prefer one over the other.
In the case of the subject URL, BrightCloud returns ‘Uncategorized’ and alphaMountain returns ‘Unrated’. These results are often returned when a domain or host has been shut down or otherwise decommissioned from its original purpose. In our case, given the elapsed time between delivery of the SMS spam or phishing and our analysis of the URL, these results are expected as the content has been removed from the site.
Factors Shown
Factors (or ‘Influences’ as BrightCloud refers to them) are the inputs that go into the determination of a domain’s risk. Threat factors provide useful context to analysts during the course of an investigation so that they can make informed, data-driven decisions as to any next steps they might take.
For the subject URL, BrightCloud indicates three factors: one positive and two negative. alphaMountain indicates six factors: two ‘High Risk’, four ‘Warning’, and zero ‘Low Risk’. Whereas alphaMountain’s three-tiered threat factors are individually color coded, BrightCloud’s are binary: red for negative influences, green for positive influences.
Related Hosts
BrightCloud URL or IP Lookup does not offer any information regarding hosts related to your query. As previously mentioned, it is not clear through this portal as to whether or not they do ultimately provide this contextual threat intelligence in one of their services
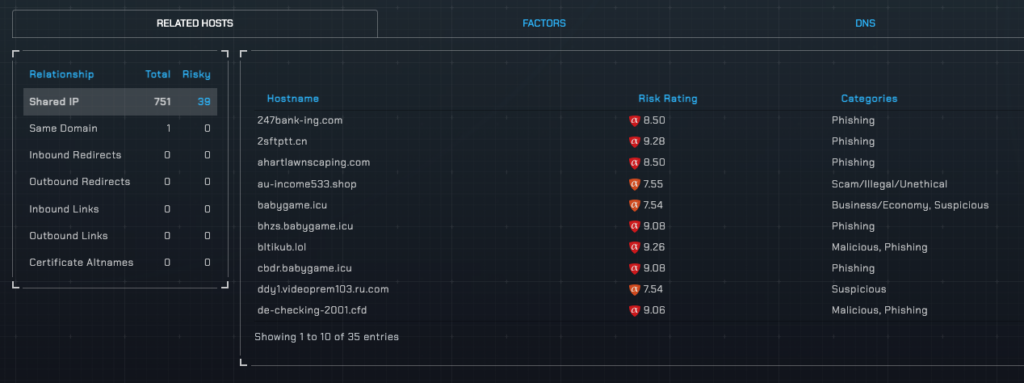
Related Hosts to initial URL query in threatYeti
On the free tier, alphaMountain’s threatYeti threat research platform shows that the subject URL is related to at least 780 other hosts, 39 of which are flagged as ‘malicious.’ This relational context is critical to threat investigations so that the entire estate of malicious domains can be rationalized in one place. threatYeti allows you to pivot into any of these domains and their IP space for deeper threat research.
DNS
When looking at the DNS information for this query, BrightCloud returns the canonical names for the nameservers, in this case luke.ns.cloudflare.com and galilea.ns.cloudflare.com. If you were using this same BrightCloud service in an actual investigation, you would need to run another lookup elsewhere to see the IPs to which these names resolve.
alphaMountain returns the country location of the DNS service, and IP addresses including IPv4 and IPv6 addresses for the servers as applicable. Additionally, alphaMountain displays the service provider’s name. In the event this isn’t clear from any resolved IPs, this saves analysts time should they need to issue a takedown request or otherwise need to know who to contact.
Certificates
BrightCloud does not offer certificate information in their URL or IP Lookup tool. Again, this may be available in other versions of their threat intelligence services, but it is not shown in this solution of theirs.
alphaMountain does return certificate information in threatYeti, however in this case it is shown as ‘Unavailable’. This is likely due to the site already being taken down and no certificate being present. On this free version of threatYeti you would see ‘Valid’ if indeed a valid certificate were present on the domain. By signing up with an email address and creating a free ‘Community’ account, you will have access to not only the certificate chain, but the certificate redirect chain and responses as well.
Redirects
BrightCloud analyzes the URL or IP address verbatim as entered for the query. It appears that no subsequent action is taken programmatically on the url, and no redirect chain intelligence is generated. Again, it is possible that BrightCloud offer this service, but it’s not in their URL or IP Lookup.
alphaMountain displays the redirect chain for the URL. It is common practice for the threat actors behind phishing, malware and other malicious campaigns to redirect initial benign URLs to malicious hosts in order to pass through spam filters and network security policies. alphaMountain shows that this random SMS campaign in our inbox indeed forwarded the recipient’s initial click to a server running a .php script on Google Cloud Platform. Naturally, if you are investigating this campaign or one like it, and this ultimate host is indeed malicious (which alphaMountain will also show you) this is invaluable information for rapidly implementing security policies that will prevent all URLs in the chain from impacting your organization.
Conclusion – A BrightCloud Alternative
Between BrightCloud’s URL or IP Lookup and alphaMountain’s threatYeti domain research platform, both offer threat researchers the ability to quickly ascertain more information about the risk of a host. For a simple assessment or validation of risk that requires no further investigation, BrightCloud is probably sufficient in many cases. As one would expect, this free tool from BrightCloud is likely a watered down version of what is available via their premium Threat Intelligence Services API. A full assessment of that solution would be in order for anyone evaluating their threat intelligence options. The alphaMountain URL threat intelligence database is gaining steam as a compelling BrightCloud alternative for many security solutions providers. Organizations routinely cite the freshness and fidelity of alphaMountain’s categorization and threat verdicts as reasons they’ve made the switch.
Naturally, we are biased, but we designed the threatYeti platform to be of immediate and significant value to professional threat analysts at any level, even on our free plan. As you have likely already garnered from reading this reasonably-objective review, we have packed a lot of domain intelligence into a very compelling package with threatYeti. All that said, there’s no better way to convey any of this value than by you trying it out for yourself. You can run queries right away, or unlock more features with a (still free) community or premium account. Compare features and editions here, and reach out if you have any questions or ideas for how to make threatYeti more useful to you.