Phishing detection is a fast-moving game of cat and mouse. We recently received a message from the popular QuickBooks accounting software which turned out it was a phishing scam. Let’s take a deep technical dive into how threat actors are leveraging legitimate services to evade legacy phishing detection solutions. Then we’ll show you how alphaMountain can help improve your phishing detection rates.
TL;DR
Modern phishing detection is a team sport: your security tools extract links (including QR-code destinations) and follow redirects; alphaMountain supplies the real-time domain and IP threat verdicts they enforce. In this QuickBooks run, the flow is: SendGrid tracking → real Intuit e-sign URL → QR in a PDF → Microsoft-style credential harvest. We’ll show you where to query alphaMountain at each hop and the policies to trigger.

Phishing Campaign Overview
A legitimate QuickBooks notification arrived in our inbox. Note the correct company name in the email subject.
Clicking the ‘Review’ link goes to a redirect URL, likely from the legitimate QuickBooks account’s integration:
https://u35120043.ct.sendgrid[.]net/ls/click?upn=u001.dQLY9BwUcXU6-2FXeHg95aoSbnoxXQMd9EmKkE98ociqx27OoR-2FRXmmvxHWgQ37e4X1Z0XYF-2F81oki4pPyveLqG72qIJGuc6-2B8OOR-2FO4kgZw484K7zL45cFlZGdJz-2FMgZYQKP9_Z3TajlUtE4b6rUs5drE3HPcmwwiA0TC-2Fb4xTaUyAYpRIcszoEELBTaUDt6-2Fg-2F2-2FjXJMfjnRs2Fd6jvIkvomSjw3en5t3jvFtftgOWZUw-2FDOCUELt0QRxELebO4mS4oywUVdIVg2J-2FQsNhUAq0lOkp5Yfe8s1q0ryG7iqrP0irJG-2FcnzwfWNSmdPU7pbuYCDJbdVsjgmEZ6wvS6uLZydcX9bDSIHYoCqNR6j8vTNOmLfhbG-2FW0ZBtGCUSD9xscbliyc9AeD4C0XQYe3wuGAtTpRRDDHETaZg8cPd8slTLz2Oobw5E9PkUalaIJFz79q8EYMQ443mS6UPVJG-2F9jT1-2B6uhfh5FAf0DZQf1EUnzfhkSJPdmzAKJWoH1jjz4BPT2mHVczwv58tZCvBfIis00uqgqJCtHjLU5ElboPaEmlc1ocjKtm7f9-2Bxxzfn1895NC0LHvd6cwuIo383v6SpjC2eBv8qChiHBXLK9p2yrm3lh6cPZ-2BgBlUEuj2Q9GpwpkvMW84Eu6c-2FKZl7N3jd9VyWMn-2Bv8vjNFM543g-2BPgQOxs6IcRFOkZhK32VHPK7D-2BSjxCgVmTVyyem2msjnlL05m0X2F659e29CyZEg-2FJiKVPsPszz0FfCpUC-2Bkz3b7MPWQ8MfRapgg1fxqqD-2BRHYjykmq6aJTzzhTj2g82sfkEwwHYunsQnSVS1-2FmpcbWrgdXzpC-2FtusXZgQ5KG-2B-2BErNjd32D4jiU0XWKs3y00RQmeHQ3sTpgYqim8u-2BqF9tp0KPi0BawdkSNL5ntrBFSbO5cuHLA5wdobQt01L6Y3nTW6DUk-2BQBReASApFTOpyjVePK85rw4K2m5qETxL6ABjTeh7u3b-2BtMG7tD-2B6CWbO-2BsabFTJKrwtbpq-2B4KFVkrg6oivRzi6Gks0TOyp3R-2FTMBcau0g5tNqZ08tM2J8aIMcdXQb9dNOI00sd5EOZXqV6pG-2BonEblYxZAZa8hR5ri15sevk-2FBlulcf9lmRACShd9Cm57ARazPMuiV16KZKt-2FqiI09LftH
The redirect destination is a legitimate QuickBooks e-signature page:
https://client-portal.app.intuit[.]com/esign?refId=8ea6499b-02c7-4c9d-897f-93b4c9e67a1e

Note the reference to company name and document ID consistent with the email’s subject line.
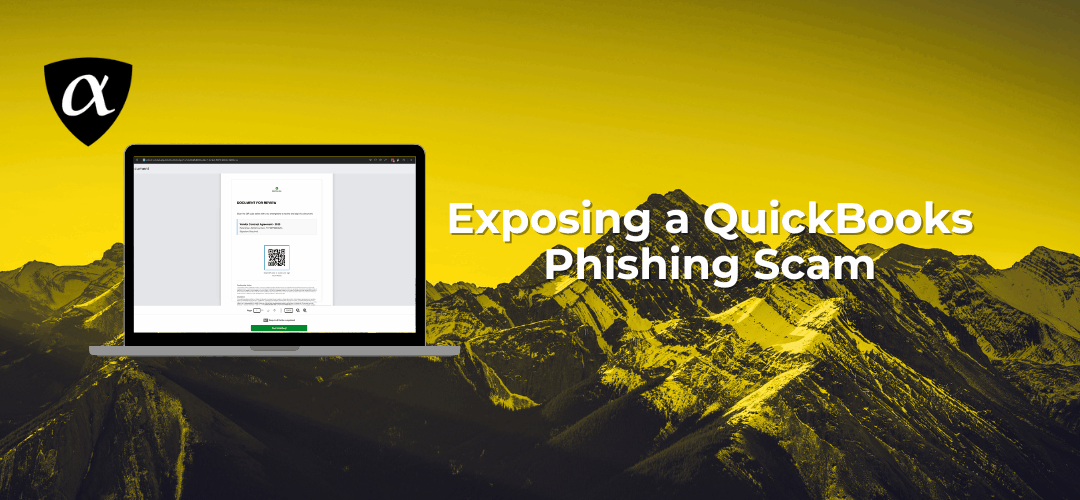
The call to action in the e-Signature portal is “Scan the QR code below with your smartphone to review and sign this document.”
This is a common method for signing documents as many people prefer using a smartphone for its ability to capture a hand-written signature–sneaky!
The link in the QR code goes to…
https://invitations[.]powerappsportals[.]com
…which then redirects to:
https://asw.tucraidrai.sa[.]com/6nFOj@neEpganhRtDDOLqtvWG/
At this stage it provides a ‘CAPTCHA’ which, despite its unfamiliar branding, will lead one to click it:

Clicking the ‘CAPTCHA’ redirects to…
https://asw.tucraidrai.sa.com/ucvzhb87yl?cc91423f180e2-41e3d83077a2ad1fc018a63dd347-0999143773e9136bef69901728df-27f9dbc0a2b7c321b1dd2ce2cd2/
…which is where the credential harvesting would take place on this fake Microsoft login page.

With that overview out of the way, let’s take a deep dive on the campaign and offer some insights into its evasion tactics and exactly where alphaMountain can be deployed to facilitate effective phishing detection in similar campaigns.
Executive summary
We analyzed a live QuickBooks “Electronic Signature” lure that strings together trusted infrastructure—SendGrid tracking, a genuine Intuit eSign URL, and a QR code inside a PDF—to evade email defenses and steal Microsoft 365 credentials. The chain looks legitimate until the final impersonated login. Effective phishing detection requires per-hop URL verdicts your tools can apply in real time.
Where alphaMountain fits in phishing detection
-
Extraction happens in your stack: SEGs, sandboxes, and proxies locate links in emails/PDFs, resolve QR codes, and follow redirects.
-
alphaMountain scores the destinations: For every domain/URL/IP encountered, call the alphaMountain API to get a single, real-time verdict, 89 category labels, and context (pDNS, related hosts, GeoIP).
-
Your controls enforce policy: Gateways, XDR/NGFW, or SOAR playbooks block, quarantine, or step-up auth based on our verdicts and categories—no body/content parsing from us required.
-
Redirect chains: Your tool follows each hop; alphaMountain returns a verdict per hop, so you can fail fast at the first risky domain
Phishing detection across the kill chain (with alphaMountain in the loop)
1) Initial lure (email layer)
Your SEG identifies the message and extracts any URLs/attachments; the legitimacy of QuickBooks/Intuit helps the lure dodge basic spam heuristics.
2) SendGrid tracking link
CTA routes through ct.sendgrid[.]net. When your SEG/proxy resolves it, query alphaMountain for a verdict on each resolved hop. If downstream risk ≥ policy or categories indicate Suspicious, Malicious, or Phishing, quarantine or rewrite the click. Evidence of the tracked link is present in this campaign.
3) Legitimate Intuit eSign hop
Redirect lands on a real Intuit eSign URL (client-portal.app.intuit[.]com/esign?...) that displays a PDF. Expect a benign verdict here; do not block legitimate infrastructure solely on reputation—continue evaluating the next hops.
4) The pivot: PDF with a QR code
Instead of collecting a signature, the document instructs users to scan a QR code. Your sandbox/SEG extracts the QR destination (e.g., invitations[.]powerappsportals[.]com) and calls alphaMountain for a verdict. If risk or categories (e.g., Newly RegisteredSuspicious) breach threshold, block or step-up auth before the user authenticates. The chain in this case clearly shows the QR pivot and downstream redirects.
NOTE: Because the pivot directs the user to change devices, if your SEG doesn’t call alphaMountain, your SWG should. This will prevent any undetected phishing links from being accessed on other networked devices should a dangerous link evade detection thus far.
5) Final lure host
For off-brand hosts like asw.tucraidrai.sa.com, alphaMountain’s aM Intelligence API can return verdict + categories + pDNS or related-host context so your SOAR can block, isolate, or expire tokens as appropriate. This host is the credential-harvest destination in the observed run.
Why legacy phishing detection fails here—and how alphaMountain helps
-
Reputation daisy-chaining: Clean brand hops hide a dirty final host. Fix: Your tool follows the chain; alphaMountain provides verdicts each hop so you can stop at first risk.
-
Mobile/QR bias: Users scan QR codes from PDFs; once your sandbox extracts the QR URL, alphaMountain scores it instantly for policy enforcement at the edge.
-
Attachment blind spots: PDFs slip through; after extraction, our feed/API supplies verdicts + categories to enforce without manual triage.
-
Ops overload: Many disparate signals slow decisions. Fix: alphaMountain’s single risk rating + human-readable threat factors + context simplify SOAR automation.
Indicators of compromise (IOCs) from this run
-
Tracked redirector:
u35120043.ct.sendgrid[.]net/ls/click?... -
Legitimate intermediate (do not block wholesale):
client-portal.app.intuit[.]com/esign?refId=… -
QR code URL:
invitations[.]powerappsportals[.]com -
Final lure hosts:
asw.tucraidrai.sa.com/...
Analyst playbook (extractor-first, alphaMountain-verdict second)
Email/SEG (email phishing detection)
-
Extract all URLs from body/headers/PDFs (vendor capability).
-
For each URL, call aM Intelligence; if verdict = malicious or category ∈ {Phishing, Malware, Suspicious/Newly Registered}, quarantine.
-
If first hop benign but downstream hop malicious, rewrite or block at click time.
Proxy/CASB/XDR (redirect-aware real-time phishing detection)
-
Follow redirects up to N hops (tool capability).
-
Query alphaMountain per hop; block on first risky verdict.
-
If benign brand → non-brand final host with risky verdict, isolate session and alert.
SOAR (incident automation)
-
Trigger when alphaMountain verdict ≥ threshold.
-
Enrich with related hosts + pDNS + GeoIP to map the infrastructure family.
-
Contain: revoke sessions, block domains, and auto-close benigns based on low-risk verdicts.
Phishing detection with alphaMountain–data you can automate on
-
Real-time URL reputation & verdicts: Query aM Intelligence API for any URL/domain/IP your controls encounter; use the single, high-fidelity risk rating for policy.
-
89 content categories: Build granular policies (e.g., Newly Registered, Suspicious, Anonymizers, Phishing/Malware).
-
Context for triage: Threat factors plus pDNS/related hosts/GeoIP help link hops to final lure domains and automate decisions.
-
Freshness & licensing: Hourly updates with Real-Time fallbacks and OEM-friendly, usage-based licensing for integration into SEG, proxy, SOAR, XDR, and TIP workflows.
Conclusion
The QuickBooks QR-code phish is a blueprint for attacks built from trusted parts. If your defenses score URLs in isolation, you’ll miss it. Phishing detection must be sequence-aware and real time: your tools extract and follow each hop; alphaMountain provides the single risk rating, 89 categories, and contextual intelligence needed to automate confident block or quarantine decisions across SEG, proxy, SOAR, XDR, and TIPs.
If your organization could use a boost in phishing detection, request your free trial of the alphaMountain API today, or go ahead a book a demo.