What Is a Threat Intelligence Feed?
In the context of web security, a threat intelligence feed is a continuous stream of contextual data that identifies malicious domains, URLs, IPs, and associated threat indicators. These feeds help security systems—like firewalls, SIEMs, TIPs, SOAR, and XDR—to detect and block emerging threats in real time.
Why Choosing the Right Feed Matters
Not all feeds are equal. Key factors that impact a feed’s value include:
- Freshness – How quickly new threats are detected and shared
- Context & fidelity – Depth and relevance of the data provided
- Scalability & integration – Ease of deployment across systems
- Coverage – Breadth and depth across domains, URLs, and IPs
Choosing a feed with real-time updates, rich signals, and seamless integration can drastically improve detection rates, reduce alert fatigue, and streamline investigations.
1. Real-Time and Hourly Updates
Cyber threats evolve at machine speed. Choose a feed that’s continuously updated, with hourly refresh cycles, and real-time fallback capabilities.
- At alphaMountain, for example, we update our feeds hourly, and can score new domains or IPs within seconds of detection.
- Fast updates ensure your detections are always ahead of emerging threats, and this is especially critical for fast-propagating phishing or malware campaigns.
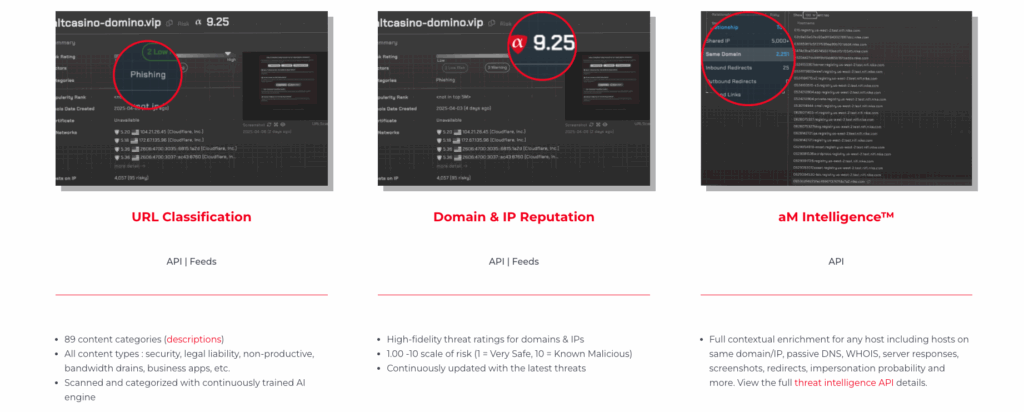
2. High-Fidelity Risk Ratings & Behavioral Context
A strong feed doesn’t just flag threats; it explains why an asset is risky. Look for:
- High-fidelity scoring – granular risk levels (e.g., 1.00–10.0 risk scale)
- Behavioral signals – features such as Domain Generation Algorithm (DGA) probability, phishing risk, and impersonation likelihood
alphaMountain uses proprietary ML/LLMs to score domains, URLs, and IPs in context, providing behavioral insights unavailable in legacy feeds.
3. Contextual Enrichment Beyond Reputation
Beyond binary malicious/benign indicators, effective feeds include:
- Content classification – e.g. 89 categories for URLs
- Passive DNS, WHOIS, server responses, screenshots, redirects
- Related host indicators and popularity metrics to help with triage
This rich context speeds incident investigation and threat hunting, enabling precise response actions.
4. Broad Data Coverage
Your feed should cover multiple dimensions:
- Domain intelligence
- URL classification and context
- IP reputation
- Feed vs. API access
We offer APIs and downloadable feed formats, suitable for both real-time use and bulk ingestion.
5. Easy Integration with Security Ecosystem
A threat feed is only as useful as its integrations:
- Out-of-the-box support for major systems like Splunk, Cisco XDR, Fortinet SOAR, and Cyware
- RESTful API allowing many integrations in under a day
- Flexible deployment modes: realtime API calls, batch feeds, or optional local DB install
6. Transparent Pricing & Licensing
Avoid surprising costs or restrictive terms:
- Look for usage-based or royalty models with flexible licensing tiers
- We offer clear granular pricing that scales with usage, ideal for platforms such as SWG, DNS, VPN, EDR and service providers such as SOCs, MSPs, threat hunting
7. Developer-Friendly, Human-Friendly Support
Changing or adding threat intelligence feeds shouldn’t require more work:
- Comprehensive documentation and support
- Our customers often integrate in a few days with expert support
8. Actionable Threat Signals for Automation
Feeding threat data into automated workflows is essential for scale:
- Combine feeds with SOAR tools like FortiSOAR or Swimlane using pre-built connectors
- Automate playbooks for score retrieval, domain impersonation checks, log enrichment, and alert triage
- Filter by risk thresholds, categories, or indicator types to surface only the most relevant signals
9. Reputation & Category Model Updates
Robust feeds rely on constantly retraining models:
- Blend live web crawling, telemetry, DNS, and other signals, some public, some private
- Thousands of new data points daily ensure evolving threats are captured, not outdated
- Transparency in threat factors and retraining is a big plus
10. Vendor Track Record and Trust
Feed providers should have strong industry adoption and partnerships:
- alphaMountain is integrated into VirusTotal, Cisco SecureX, Splunk, Maltego, and Fortinet
- Recognized by Gartner as an alternative to legacy providers, though fewer published reviews
Guide Summary: How to Compare Feeds
| Criterion | Questions to Ask | What alphaMountain Provides |
| Update Frequency | How soon are new indicators updated? | Near-real-time, hourly feed updates |
| Risk & Behavior Scores | Are risk levels granular and contextual? | 1.00–10.0 scale, phishing, DGA, impersonation signals |
| Contextual Enrichment | Do you get metadata, categories, related artifacts? | 89 content categories, WHOIS, screenshots, redirects |
| Data Type Coverage | Does feed cover domains, URLs, IPs, APIs, bulk? | Comprehensive domain/URL/IP APIs and bulk feeds |
| Security Integration | Does it integrate with existing tools? | Connectors for SOAR, SIEM, TIP, etc. |
| Pricing Transparency | Is licensing flexible and clear? | Credir- and royalty-based with no hidden caps |
| Ease of Use | Are docs and support available? | RESTful APIs, support docs, integration support |
| Automation Capabilities | Can it be used to trigger SOAR flows, filter alerts? | Pre-built playbooks, filters via FortiSOAR integration |
| Model Methodology | Is model retraining transparent and robust? | LLM/ML-powered with live data, multiple signals |
| Vendor Credibility | Is it battle-tested with enterprise partners? | Partners: VirusTotal, Cisco, Splunk, Fortinet |
Final Takeaways
A premium threat intelligence feed isn’t just raw data. It’s the heart of your network security solutions.
- Updates fast – feeds that update in seconds or minutes beat slower legacy solutions.
- Scores smart – granular ratings and behavioral context add meaningful risk insight.
- Adds context – metadata turns indicators into actionable intelligence.
- Plays well with others – APIs, connectors, and playbooks are essential in modern platforms and SOCs.
- Enables automation – letting you filter, trigger, and automate responses seamlessly.
- Scales with clarity – transparent pricing, model retraining, and vendor trust matter.
When evaluating providers, keep us in mind. We offer hourly, contextual feeds; flexible integrations; transparent licensing; and ML-driven threat models.
Next Steps
- Request a free trial of our API
- Test within your solution or SIEM / SOAR toolchain
- Benchmark coverage, access speed, and false‑positive rates
- Build automated playbooks using filters, scores, and enrichment
- License an alphaMountain domain and IP threat intelligence feed on terms that make sense for your business
A well‑chosen threat intelligence feed is the foundation of a proactive, automated, and resilient security operation. Start your evaluation, and let it power faster, more confident decision-making.